Since Windows 8 and Server 2012, Windows has used UEFI to check the signatures on the boot drivers, firmware drivers and the OS itself to make sure the code hasn’t been tampered with (for example by a rootkit), and then launched any installed anti-malware software before launching any other code.
If you have a TPM, Windows can use it to store measurements of the boot components to pass to the anti-malware software so it knows those components were checked. Windows 10 can also use Hyper-V to protect the Windows logon process from malware (Virtualisation Based Security), although that’s something you have to turn on yourself on all but the latest Arm-based PCs.
SEE: 20 pro tips to make Windows 10 work the way you want (free PDF) (TechRepublic)
But all that assumes that you can trust UEFI and the other firmware on the PC. If the firmware itself is compromised, it can lie to the anti-malware software — and even formatting and reinstalling the OS won’t clean it off the PC. As Windows itself gets harder to attack, hackers are turning to firmware attacks, including System Management Mode (an Intel CPU feature handling power management, thermal monitoring and other hardware configuration).
Firmware comprises millions of lines of code, and it’s not just that every OEM writes their own firmware — they might have different versions of firmware for different PCs. That code runs with a very high level of privilege, it’s often hard to update, and like any other software, it’s going to have bugs. More firmware vulnerabilities are being discovered and exploited in attacks — one used the anti-theft features in firmware for locating a stolen PC to track where the user was every day, for example.
Instead of relying on OEMs’ ability to fix firmware bugs quickly, Secured-core PCs completely change the way Windows boots, by no longer trusting the firmware — only the CPU, the TPM and the Windows code.

“Given the increase in firmware attacks we’ve seen in the last three years alone, the goal was to remove firmware as a trusted component of the boot process, so we’re preventing these kinds of advanced firmware attacks,” Dave Weston, director of OS security at Microsoft, told TechRepublic.
The first line of the Windows boot loader on Secured-core PCs puts the CPU into a new security state where, instead of accepting the measurements made during Secure Boot, even though they’re in the TPM, it goes back and revalidates the measurement. If they don’t match, the PC doesn’t boot and goes into BitLocker recovery mode instead. If you’re managing the PC via Intune, it also sends a signal to the service that the device can’t be trusted and shouldn’t be allowed to connect to your network.
“These PCs use the latest silicon from AMD, Intel, and Qualcomm that have the Trusted Platform Module 2.0 and Dynamic Root of Trust (DRTM) built in. The root of trust is a set of functions in the trusted computing module that is always trusted by a computer’s OS and embedded in the device,” Weston explains. “Creating a hardware-based root of trust means we’re adding functionality at the hardware level to ensure the device boots securely and malware hasn’t penetrated the firmware.”
“The root of trust on a secured-core PC is the CPU itself. When the Windows boot loader runs, the System Guard Secure Launch invokes DTRM instructions on the CPU to remove any trust associated with firmware,” says Weston. “Measurements are made throughout the process into the TPM of the critical Windows boot components. The components being measured are a relatively small set from Microsoft and the CPU vendor, which limits the number of things we need to measure and side-steps issues like keeping track of OEM/firmware vendor code.” That avoids Secure Boot slowing down startup.
Windows can’t use the Dynamic Root of Trust or Secure Launch to avoid vulnerabilities in System Management Mode in the same way because it loads too early — but it’s important to protect it because it has even more privileges on the system than the hypervisor. To solve this, Microsoft worked with the silicon vendors to find out what SMM needs to do and redesigned the memory paging system in Windows to lock key memory pages so they can’t be altered. SMM can still turn on the power light on your laptop, but it can no longer change memory used by the hypervisor. An attacker might still be able to compromise SMM, but that no longer gives them the ability to compromise the rest of the system.
Secured-core PCs also turn on all the optional Windows 10 security features like HyperVisor Code Integrity, which only allows signed drivers to run and prevents many Return-Oriented-Programming attacks like WannaCry.
When you lock a Secured-core PC, you can’t install a new DMA device attached over Thunderbolt until you unlock the device with a PIN or biometrics. That prevents attackers who get physical access to your machine and could otherwise plug in a malicious device disguised as a cable (which you can make with parts sold on eBay and code available on GitHub).
If you manage PCs with Intune, admins can require Secured-core PCs for access to extremely confidential documents. Intune can also look at the measurements taken to show the health of the PC while you’re using it. This means that if it’s compromised and an attacker turns off the anti-virus software so they won’t be detected, for example, that will show up as a suspicious change that conditional access polices can use to block the PC.
Weston compares that to tamper-proof seals on medicine packages: “We’ve gone from a world where I can pop one PC and laterally move through your entire network, to a world where the cloud will reject you if the CPU doesn’t believe the machine.”
Patching older PCs
There are options PC makers can take without going as far as Secured-core, like using Windows Update to deliver automatic firmware updates so any patches are applied as soon as possible. UEFI still handles the actual installation of the updates, but it means you don’t have to rely on users going to the OEM website to look for firmware updates (or admins testing and pushing them), so you’re more likely to be running the latest, most secure version of the firmware.
Surface devices already do this, and Microsoft has open-sourced the basis of the Surface UEFI firmware as Project Mu in an attempt to give OEMs a leg up with their own secure firmware. If your PC doesn’t do that, Weston suggests that “end users can reduce their risk by ensuring that UEFI Secure Boot is enabled in BIOS settings, and by routinely checking their device OEM’s website for updated firmware and drivers.”
You can also turn on Secure Launch on existing PCs with Windows 10 Pro version 1809 or later, as long as they have Intel Coffee Lake/Qualcomm Snapdragon 850 and later CPUs and TPM 2.0. It’s not on by default: you can enable it in Settings / Update & Security / Windows Security / Open Windows Security / Device security / Core isolation / Firmware protection.
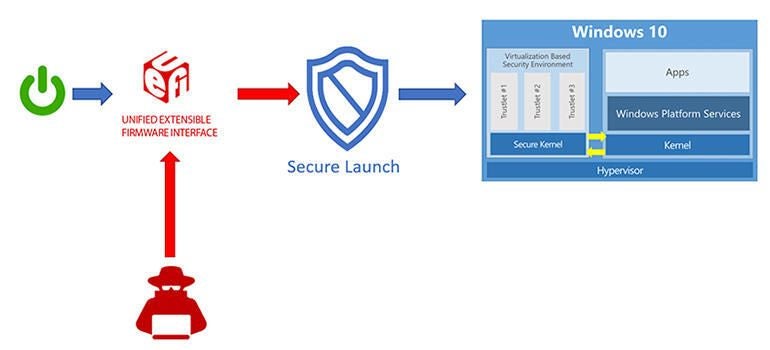
This uses the TPM as a Dynamic Root of Trust for the same measurements, delivers the same paging protection and supervision of System Management Mode, and lets you use Intune or SCCM to check for tampering the same way. If you have the right hardware to turn it on, you definitely should.
The reason Microsoft and the OEMs have worked together to create Secured-core PCs is that having security that’s turned on at the factory when the TPM is provisioned — before the PC can ever be compromised — is important for regulated companies. “These PCs are specifically designed for highly-targeted industries that handle super-sensitive data and need added, multiple layers of security built in,” Weston noted.
SEE: Cheat sheet: Microsoft Surface Pro 7 (free PDF) (TechRepublic)
Plus, they also rely on specific CPU features that older PCs just don’t have, so you may find that you don’t have systems that support Secure Launch. Similarly, if you want to use Virtualisation Based Security (which sets up several small, fast, invisible VMs on the PC for features like Credential Guard), you’d need to check if they worked on your PCs, and then check that they didn’t break any drivers or reduce performance too much. Now you can just buy a PC where you know they will work.
In fact, one of the most useful things about Secured-core PCs is that for many enterprises, selecting a PC with the right features to enable all the Windows security options is difficult because the list of devices approved for purchase in a large organization is often out of date. You need TPM 2.0 to make BitLocker and Windows Hello as secure as possible, and to store other encryption keys. Just having a label like this will make it easier to pick a PC that can take advantage of the security features that are already in Windows.