Contents:
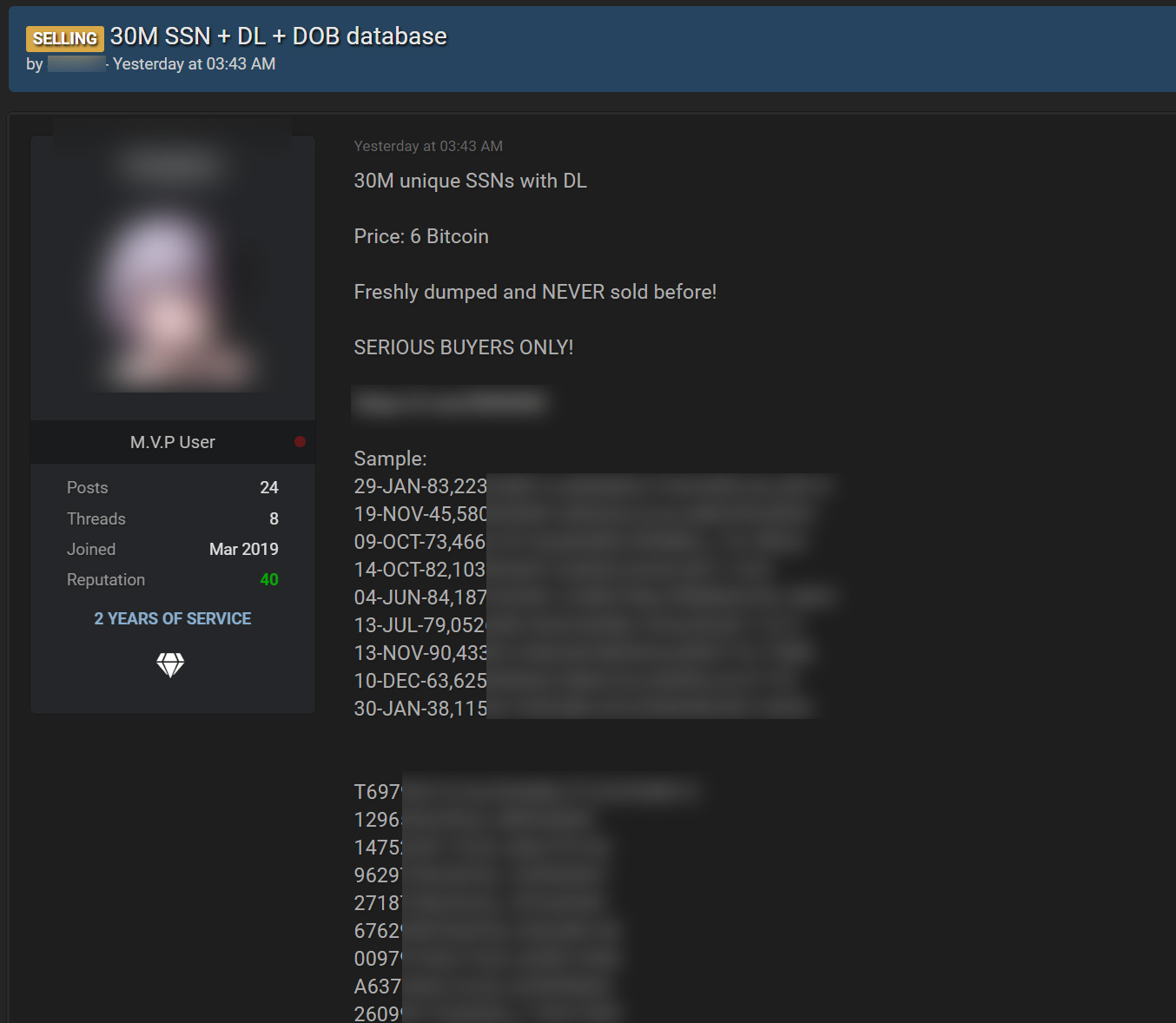
On August 14, 2021, a database holding the data of 30 million consumers was put up for sale on a hacker site for six bitcoins ($280K).
The threat actors had targeted T-Mobile servers involved in development, staging, and production.
To prove the authenticity of the T-Mobile data breach, threat actors shared a print screen of an SSH connection to an Oracle production server.
What Happened?
As BleepingComputer reported, the notice from the New York State Office of the Attorney General comes after people affected by the event were told by identity theft protection services that their information had been discovered online, suggesting that affected customers are now at a higher risk of identity theft.
According to the NY OAG’s recommendations, customers who are at risk should utilize credit monitoring services to be notified within 24 hours of any changes, such as major transactions or newly opened accounts.
NEW YORK – New York Attorney General Letitia James today provided guidance to consumers who may have been impacted by a 2021 T-Mobile data breach, following reports that the stolen information was put for sale on the dark web. Alongside a bipartisan coalition of attorneys general, Attorney General James advised all New York residents who believe they were impacted by the data breach to take appropriate steps to protect their information from identity theft. This comes after several individuals received alerts that their information was circulating online following the August 2021 data breach.
“I have an urgent message for T-Mobile customers and other consumers: Be aware of any misuse of your personal information and follow the guidance provided by my office to protect yourself from identity theft,” said Attorney General James. “Information stolen in a massive data breach has fallen into the wrong hands and is circulating on the dark web. The guidance offered by my office can help prevent identity theft. I advise all New Yorkers to maintain their financial safety by following the guidance my office has laid out. No consumer should have to deal with the devastating realities of identity theft.”
They’re also advised to consider putting a free credit freeze on their credit reports (through Equifax, Experian, or TransUnion) to prevent identity thieves from creating new credit accounts with stolen personal information.
Attorney General James urges anyone who believes they were impacted by the T-Mobile breach to take the following steps to protect themselves:
Monitor your credit.Credit monitoring services track your credit report and alert you whenever a change is made, such as a new account or a large purchase. Most services will notify you within 24 hours of any change to your credit report.
Consider placing a free credit freeze on your credit report. Identity thieves will not be able to open a new credit account in your name while the freeze is in place. You can place a credit freeze by contacting each of the three major credit bureaus.
The breach was verified by the US mobile provider, who subsequently said that the attacker obtained data from 54.6 million current, past, or prospective customers.
Fortunately, the attacker did not take any consumer financial information, credit card information, debit, or other payment information during the incident, as T-Mobile reported.
T-Mobile CEO Mike Sievert said at the time that the business has blocked the access points used to brute-force through the carrier’s network and promised consumers that “there is no continuing danger to customer data as a result of this hack.”
On August 17th we confirmed that T-Mobile’s systems were subject to a criminal cyberattack that compromised data of millions of our customers, former customers, and prospective customers. Fortunately, the breach did not expose any customer financial information, credit card information, debit or other payment information but, like so many breaches before, some SSN, name, address, date of birth and driver’s license/ID information was compromised. To say we are disappointed and frustrated that this happened is an understatement. Keeping our customers’ data safe is a responsibility we take incredibly seriously and preventing this type of event from happening has always been a top priority of ours. Unfortunately, this time we were not successful.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










