As a security professional, you spend your waking hours thinking of every possible way to defend your organization from cyberattacks.
You can be doing everything right, but sometimes hackers still find a way to gain access to your most critical information. In many cases, a simple click on an email from one of your end-users is all a hacker needs.
Phishing attacks hit an all-time high earlier this year, and your end-users should certainly be trained on how to identify them.
The Anti-Phishing Working Group (APWG) has released its Phishing Activity Trends Report, 1st Quarter 2021, which dives into phishing attacks and other identity theft techniques.
Phishing activity doubled in 2020, largely due to the pandemic and remote work, and continued to climb in the first month of 2021.
APWG tracks three statistics for phishing attacks: the number of unique phishing web sites detected, unique phishing email subjects, and the number of brands targeted by phishing campaigns.
Here are those numbers from January 2021:
- Number of unique phishing Web sites detected: 245,771
- Unique phishing email subjects: 172,793
- Number of brands targeted by phishing campaigns: 430
BEC attacks on the rise
If you are paying attention to the cybersecurity news cycle, every day you hear ransomware this and ransomware that and that ransomware can bring your organization to a crumble.
While this is certainly true, there are other types of attacks that are also incredibly successful right now.
One that you don't hear about as much as you probably should is BEC attacks, or Business Email Compromise.
One of APWG's members, Agari, has tracked thousands of BEC attempts during Q1 of 2021.
Researchers consider a BEC attack to be "any response-based spear phishing attack that involves the impersonation of a trusted party to trick a victim into making a financial transaction or sending sensitive materials."
The numbers Agari has discovered are quite staggering:
"Agari found that the average amount requested in wire transfer BEC attacks increased 14 percent from $75,000 in Q4 2020 to $85,000 in Q1 2021.
This increase is primarily attributed to a continued resurgence in BEC campaigns from Cosmic Lynx, a sophisticated Russian-based BEC group, as well as mergers-and acquisitions themed campaigns that have requested larger payments from BEC targets.
Agari found also that in Q1 2021, scammers requested funds in the form of gift cards in 54 percent of BEC attacks, down from 60 percent in Q 4 2020 and 71 percent in Q3 2020. The other 46 percent of requests involved bank transfer, payroll diversion, and 'financial aging requests.'
In a financial aging request, the scammer impersonates an executive and requests that someone in the target company send him a report that contain details about outstanding payments owed by the company's customers, and the accompanying customer contact details.
While aging report BEC attacks have been around for more than a year, their volume was minimal until Q1 2021, when more than 10 percent of all BEC attacks involved aging report requests."
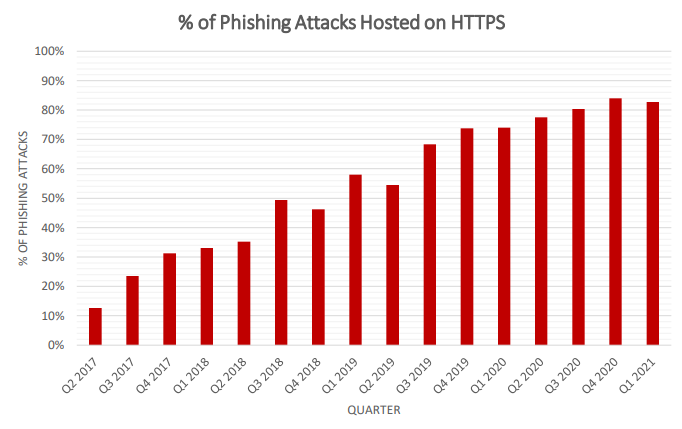
Phishing attacks using HTTPS
The report also analyzes how phishers have been using encryption to fool victims, primarily the HTTPS encryption protocol.
Here is why the Anti-Phishing Working Group looks at HTTPS:
"APWG contributor PhishLabs has been tracking the proportion of phishing sites that are protected by the HTTPS encryption protocol. HTTPS is used to secure communications by encrypting the data exchanged between a person's browser and the web site he or she is visiting.
HTTPS is especially important on sites that offer online sales or password-protected accounts. Studying HTTP on phishing sites provides insight into how phishers are fooling Internet users by turning an Internet security feature against them."
The following chart is included in the report to show the portion of phishing attacks on HTTPS:
SecureWorld resources for cyber threats
SecureWorld has a number of resources to help better secure your organization. Here are some upcoming webcasts that can help.




