Despite a very slim browser market share, Internet Explorer (IE) is still being exploited by exploit kits like the RIG exploit kit (EK).
One major advantage for the malware distributors behind the exploit kit is that the outdated browser has reached end-of-life (EOL), which means it no longer receives security updates and patches against known threats.
According to Malwarebytes’ Senior Director of Threat Intelligence Jérôme Segura:
“RIG EK is probably one of the last exploit kits targeting Internet Explorer still around. We have observed RIG EK activity via the same malvertising campaigns for the past several years.”
An exploit kit is a toolkit designed to facilitate the exploitation of client-side vulnerabilities most commonly found in browsers and their plugins in order to deliver malware. The primary infection method with an exploit kit is a drive-by download attack, when cybercriminals lure potential victims to a site where their browser can be fingerprinted and vulnerabilities can be unleashed to infect the system. Ideally for the exploit kit handler, such attacks occur silently within seconds and they do not require any user interaction.
A recent report by Prodaft details a wealth of information related to the victim statistics, operation, command and control (C&C) server, and technical aspects of RIG EK.
RIG EK has been around since 2014 and, despite many take down efforts, has always managed to make a comeback. Without many changes to the inner workings of the exploit kit itself, we’ve seen many changes in the malware distributed. It all depends on which cybercriminals pay the RIG EK administrator to install their malware on victim machines. RIG EK has also introduced some newer vulnerabilities while Internet Explorer’s market share has continued to drop.
Prodaft researchers describe how they noticed RIG EK RIG dropping multiple types of malware, including stealers, Remote Access Trojans (RATs), cryptocurrency miners, and banking malware. The exploits of RIG EK are delivered to unsuspecting victims in two ways: either via malvertising, where users are redirected to online advertising pages that are tricked to execute the RIG exploits on their browser; or when the victim visits sites that were compromised and the exploit kit’s JavaScript was injected.
As Jérôme mentions, at Malwarebytes we’ve seen them involved via the same malvertising campaigns for the past several years.
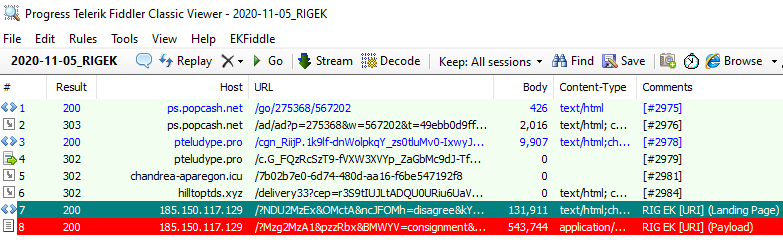
2020 analysis of malvertising leading to the RIG Exploit Kit
We connected some RIG EK activity with the cybercriminal behind the “MakeMoney gate” (a name coined by security researcher @nao_sec) based on the domain makemoneywithus[.]work (188.225.75.54) with the earliest instance of this threat group seen in December 2019 via the gate gettime[.]xyz (185.220.35.26).
We still see some hits every week, but nothing to make this exploit kit a real threat anymore. We should note that the threat actor behind the MakeMoney gate tried the social engineering route in 2022, using a fake browser update campaign which was not all that different from the one we saw with SocGholish.
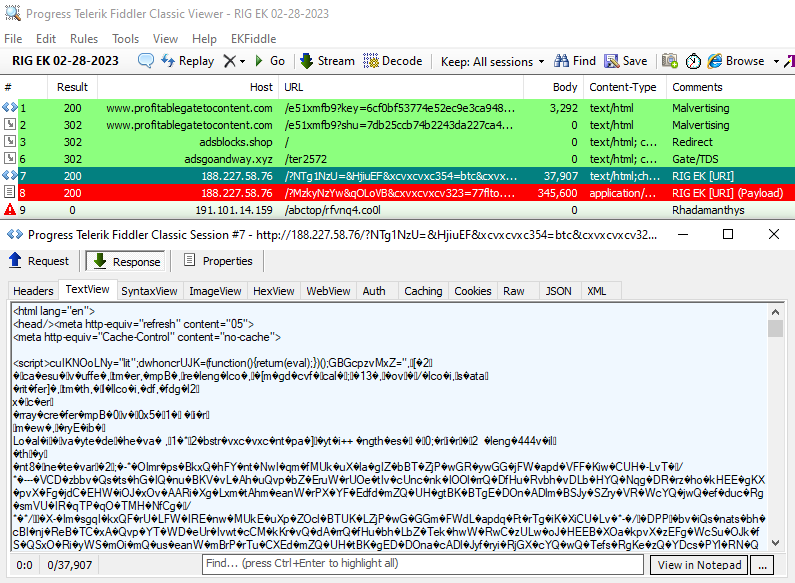
Very recently recorded malvertising campaign
Mitigation
The main advice to stay out of the claws of exploit kits is clear. Use a fully updated and patched browser. And always be careful before you click on links.
A warning from Jérôme Segura:
“We can expect RIG EK to stick around to the very end until there is no one left behind to infect. The individual(s) behind the malvertising campaigns have been persistent and still count on victims daring enough to visit shady websites with an outdated computer.”
Have a burning question or want to learn more about our cyberprotection? Get a free business trial below.











