
A new report from Kaspersky sheds light on the 2020-2022 ATM and Point of Sale (PoS) malware landscape.
The COVID-19 effect
Lockdowns all around the globe during the pandemic have seriously reduced ATM and PoS malware activity, since people stayed at home with no other possibility than buying what they needed online instead of physically going to shops.
In 2020, the number of attacks on ATM/PoS dropped significantly in comparison to 2019, from approximately 8,000 attacks to 4,800 (Figure A).
Figure A
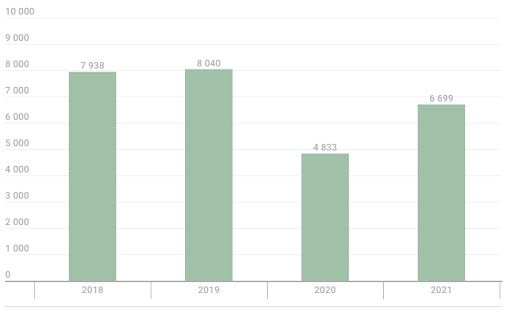
While the lockdowns saw a lot of devices being turned fully off, another reason explaining this drop is the global number of cash machines tending to decrease, as explained by the researchers.
In 2021, a 39% increase of the attacks was observed, showing that the COVID-19 restrictions had been dropped down, allowing customers to return to their usual consumer habits.
SEE: Mobile device security policy (TechRepublic Premium)
Most targeted regions for ATM/PoS malware attacks in 2020-2022
From 2017 to 2021, Russia has always been the most impacted country. Outdated fleets of ATMs made it fairly easy for attackers to gain access and steal money from those devices, as the outdated equipment was vulnerable to most malware families and generally had a low level of cybersecurity, according to Kaspersky. Brazil has been in the same situation, with an outdated ATM fleet, yet in addition Brazil has a number of cybercriminals creating new POS malware there.
Zimbabwe appeared in the top five in 2021, and is still there in 2022. A reason for this, as explained by Kaspersky, is that Chinese investors are opening new businesses in that country, generating economic growth and becoming attractive for cybercriminals.
Main types of malware activity
Two malware families stand out in Kaspersky’s analysis: HydraPoS and AbaddonPoS (Figure B).
Figure B
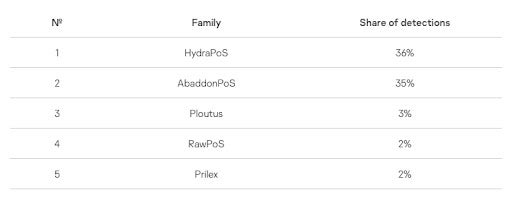
HydraPoS
HydraPoS still holds its leader position, although no new version has been released recently. This malware originates from Brazil and is notorious for cloning credit cards. HydraPoS combines several pieces of malware binded with a handful of legitimate third-party tools.
To have HydraPoS being installed on devices, cybercriminals make use of social engineering. They call companies on the phone and pretend to be employees from a credit card company. Once trust is established, they ask the victim to access a website and install an update, which in fact launches the infection, providing access to the fraudsters.
AbaddonPoS
AbaddonPoS has been active since 2015 and is a generic PoS malware that tries to hide its activities via anti-analysis mechanisms, code obfuscation and a custom protocol for exfiltrating data from the victims to the cybercriminals.
Ploutus
Ploutus is one of the most advanced ATM malware. It first appeared in 2013 yet it keeps evolving via new versions and targets organizations such as ATM manufacturers, especially in Brazil. The malware enables the attacker to modify the legitimate software running on ATMs and execute privilege escalation to get control of the ATMs, allowing the cybercriminals to physically cash out from ATMs on demand.
RawPoS
RawPoS is one of the oldest PoS malware in the scene. It has been in use since 2008, and allows the extraction of full magnetic stripe data from volatile memory.
Prilex
Prilex is a Brazilian threat actor who switched from ATM-focused malware to PoS malware in 2016. Prior to this move, the group has been responsible for one of the largest ATM attacks in Brazil, stealing money from more than 1,000 machines while also cloning 28,000 credit cards that were used in these ATMs. The Prilex PoS malware evolved into a very advanced and complex malware capable of modifying communications with the PIN pad and bypass EMV (Europay Mastercard Visa) validations. The cybercriminals behind that malware adopted the malware-as-a-service business model, selling it for about $3,500 on underground cybercriminal marketplaces.
SEE: Password breach: Why pop culture and passwords don’t mix (free PDF) (TechRepublic)
Unsuspecting victims
It seems companies using PoS devices often blindly trust the software on it, and tend to be unaware of the possibility of having malware on it that would steal all the information that can be stolen by cybercriminals. Part of that trust is legitimate: the payment card industry uses several security standards enforcing end-to-end encryption of sensitive payment data, amongst other security measures, making it harder for cybercriminals. Yet if an attacker manages to execute code on those devices, he still may access the sensitive data, which is only decrypted in memory and never on other storages.
Social engineering also seems to work quite well to infect PoS devices with malware, as employees generally do not have much knowledge of all the procedures to handle those devices and may just do anything a “professional” would ask them to do.
How to protect from this threat?
Customers obviously cannot do much about this threat, so all security measures need to be deployed by the PoS devices maintainers and the ATM manufacturers.
For starters, older systems need to be updated and patched, especially those running outdated versions of Microsoft Windows. Also, embedded security software needs to be deployed, to protect from various attack vectors and to detect threats.
Although the communications are encrypted on those devices, it might be a good idea to deploy network detection/defense solutions, which might detect unusual amounts of data being transferred, or unexpected communications to different IP addresses.
White-listing of applications can also be deployed on devices, to only allow selected software to run, making it harder for attackers to run their malware or code on those devices.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.


