An “unidentified actor” is making use of these two malicious files to cause combo-laden mayhem on desktops around the world, according to new research from Talos.
The tag-team campaign serves up ransomware known as Mortal Kombat, which borrows the name made famous by the video game, and Laplas Clipper malware, a clipboard stealer. Depending on the flow of infection, targets can expect to find a demand for payment to unlock encrypted files or sneaky malware looking to grab cryptocurrency details from system clipboard functions.
These attacks have been taking place since December 2022 and have no specific target, with small and large organisations affected, as well as individuals. The infection chain is kick-started by an email harbouring a malicious attachment.
The email is cryptocurrency themed, and claims that a payment of yours has “timed out” and will need resending. Given how long it can take some cryptocurrency payments to be processed, this is likely to raise the curiosity of recipients.
The email comes with a dubious zip attachment containing a BAT loader that begins the infection process when it’s executed. The BAT loader kicks off a chain of events that results in the download and execution of the ransomware or the clipper malware, from one of two URLs. (The analysis by Talos does not include how it decides which to deploy, so it could be targeting or just random chance.)
It’s like a choose your own adventure game gone horribly wrong.
Laplas Clipper
Laplas Clipper is a form of Trojan, and it takes a very smart approach to cryptocurrency theft. Regular clipboard-swiping malware waits for a user to copy a cryptocurrency address (which looks like a long password) and then switches it out for an address owned by the scammer. The end result is that the victim sends their payment to the attacker instead of the intended recipient.
Laplas switches out to wallet addresses which look similar to the correct, intended destination. Rather than carrying a stack of addresses with it, it phones home, contacting its Command and Control (C2) server via HTTP GET for a close match.
It’s also able to generate imitation addresses for a wide variety of cryptocurrencies including Monero, Bitcoin, Ethereum, Solana, and even Steam trading URLs. This is, of course, very bad news for people who do a lot of wallet address copying and pasting.
In this instance, it creates both persistence on the infected machine via the AppDataRoaming folder and a Windows scheduled task which means Clipper activates “every minute for 416 days”. This essentially grants non-stop monitoring of a system. It then acts as mentioned above, switching out genuine wallet addresses for bogus imitations.
Malwarebytes detects Laplas Clipper as Trojan.Clipper.
Mortal Kombat ransomware
Mortal Kombat Ransomware is based on Xorist Commodity ransomware. According to Talos, it has mainly been seen in the US, as well as the Philippines, the UK, and Turkey. This type of ransomware is created via a builder program. The builder allows for a reasonable amount of customisation, which includes warning messages, desired file extension, wallpaper addition, the file extension used on encrypted files, and so on.
Once installed on a system, Mortal Kombat targets a large selection of files for encryption, based on their file extensions. It also drops a ransom note and changes the wallpaper for the PC. According to The Record, the wallpaper features the character Scorpion from…you guessed it…Mortal Kombat.
There is nothing subtle about this particular ransomware threat. Talos notes that files in the recycle bin are not spared from attack.
Applications and folders are removed from Windows startup, and indicators of infection are discreetly tidied up and removed. The ransom note reads as follows, pushing those impacted towards communication with the attackers via instant messaging:
YOUR SYSTEM IS LOCKED AND ALL YOUR IMPORTANT DATA HAS BEEN ENCRYPTED. DON’T WORRY YOUR FILES ARE SAFE. TO RETURN ALL THE NORMALLY YOU MUST BUY THE CERBER DECRYPTOR PROGRAM. PAYMENTS ARE ACCEPTED ONLY THROUGH THE BITCOIN NETWORK. YOU CAN GET THEM VIA ATM MACHINE OR ONLINE.
Instructions are then provided to download the aforementioned chat program, add the attackers as a “friend”, and begin communication.
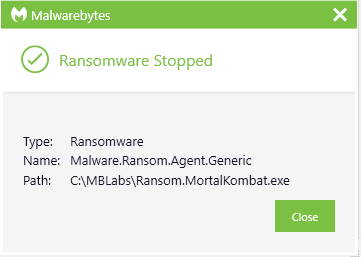
Malwarebytes detects Mortal Kombat ransomware as Malware.Ransom.Agent.Generic.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; disable or harden remote access like RDP and VPNs; use endpoint security software that can detect exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like Malwarebytes EDR that uses multiple different detection techniques to identify ransomware.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Write an incident response plan. The period after a ransomware attack can be chaotic. Make a plan that outlines how you’ll isolate an outbreak, communicate with stakeholders, and restore your systems.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.










