On Jan. 9, 2024, U.S. authorities arrested a 19-year-old Florida man charged with wire fraud, aggravated identity theft, and conspiring with others to use SIM-swapping to steal cryptocurrency. Sources close to the investigation tell KrebsOnSecurity the accused was a key member of a criminal hacking group blamed for a string of cyber intrusions at major U.S. technology companies during the summer of 2022.
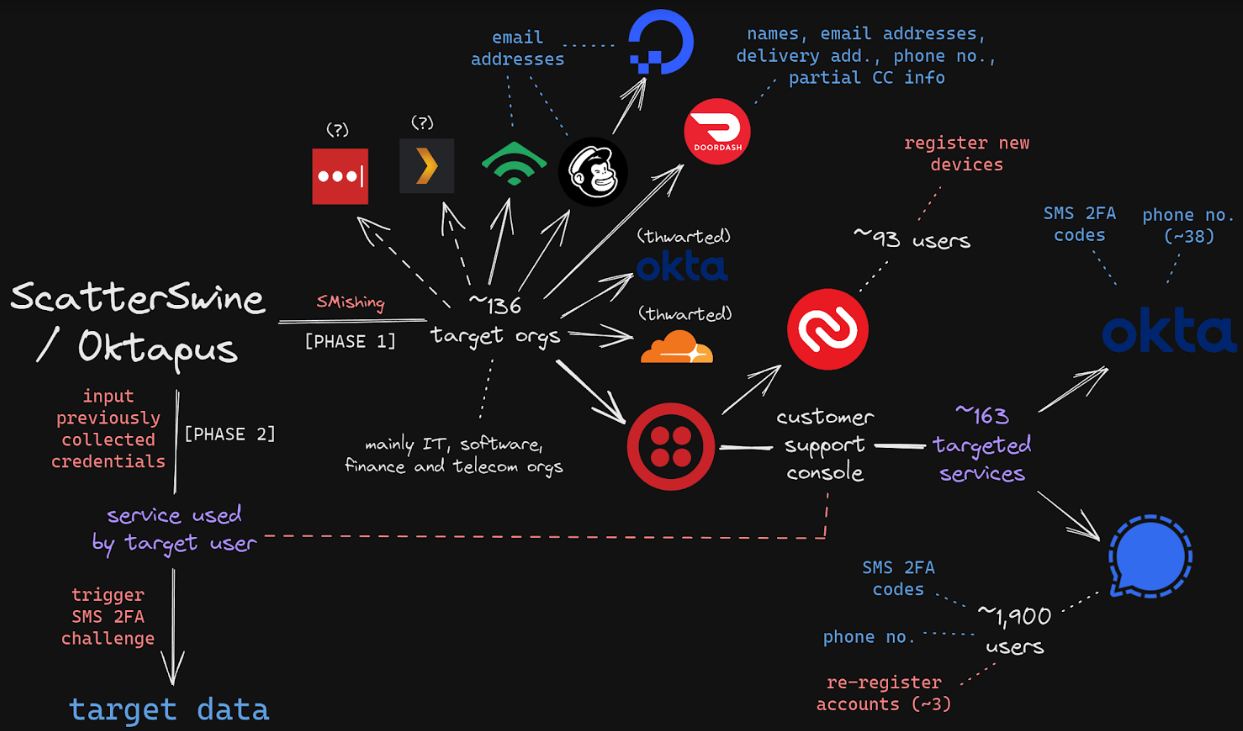
A graphic depicting how 0ktapus leveraged one victim to attack another. Image credit: Amitai Cohen of Wiz.
Prosecutors say Noah Michael Urban of Palm Coast, Fla., stole at least $800,000 from at least five victims between August 2022 and March 2023. In each attack, the victims saw their email and financial accounts compromised after suffering an unauthorized SIM-swap, wherein attackers transferred each victim’s mobile phone number to a new device that they controlled.
The government says Urban went by the aliases “Sosa” and “King Bob,” among others. Multiple trusted sources told KrebsOnSecurity that Sosa/King Bob was a core member of a hacking group behind the 2022 breach at Twilio, a company that provides services for making and receiving text messages and phone calls. Twilio disclosed in Aug. 2022 that an intrusion had exposed a “limited number” of Twilio customer accounts through a sophisticated social engineering attack designed to steal employee credentials.
Shortly after that disclosure, the security firm Group-IB published a report linking the attackers behind the Twilio intrusion to separate breaches at more than 130 organizations, including LastPass, DoorDash, Mailchimp, and Plex. Multiple security firms soon assigned the hacking group the nickname “Scattered Spider.”
Group-IB dubbed the gang by a different name — 0ktapus — which was a nod to how the criminal group phished employees for credentials. The missives asked users to click a link and log in at a phishing page that mimicked their employer’s Okta authentication page. Those who submitted credentials were then prompted to provide the one-time password needed for multi-factor authentication.

A booking photo of Noah Michael Urban released by the Volusia County Sheriff.
0ktapus used newly-registered domains that often included the name of the targeted company, and sent text messages urging employees to click on links to these domains to view information about a pending change in their work schedule. The phishing sites used a Telegram instant message bot to forward any submitted credentials in real-time, allowing the attackers to use the phished username, password and one-time code to log in as that employee at the real employer website.
0ktapus often leveraged information or access gained in one breach to perpetrate another. As documented by Group-IB, the group pivoted from its access to Twilio to attack at least 163 of its customers. Among those was the encrypted messaging app Signal, which said the breach could have let attackers re-register the phone number on another device for about 1,900 users.
Also in August 2022, several employees at email delivery firm Mailchimp provided their remote access credentials to this phishing group. According to an Aug. 12 blog post, the attackers used their access to Mailchimp employee accounts to steal data from 214 customers involved in cryptocurrency and finance.
On August 25, 2022, the password manager service LastPass disclosed a breach in which attackers stole some source code and proprietary LastPass technical information, and weeks later LastPass said an investigation revealed no customer data or password vaults were accessed.
However, on November 30, 2022 LastPass disclosed a far more serious breach that the company said leveraged data stolen in the August breach. LastPass said criminal hackers had stolen encrypted copies of some password vaults, as well as other personal information.
In February 2023, LastPass disclosed that the intrusion involved a highly complex, targeted attack against a DevOps engineer who was one of only four LastPass employees with access to the corporate vault. In that incident, the attackers exploited a security vulnerability in a Plex media server that the employee was running on his home network, and succeeded in installing malicious software that stole passwords and other authentication credentials. The vulnerability exploited by the intruders was patched back in 2020, but the employee never updated his Plex software.
As it happens, Plex announced its own data breach one day before LastPass disclosed its initial August intrusion. On August 24, 2022, Plex’s security team urged users to reset their passwords, saying an intruder had accessed customer emails, usernames and encrypted passwords.
KING BOB’S GRAILS
A review of thousands of messages that Sosa and King Bob posted to several public forums and Discord servers over the past two years shows that the person behind these identities was mainly focused on two things: Sim-swapping, and trading in stolen, unreleased rap music recordings from popular artists.
Indeed, those messages show Sosa/King Bob was obsessed with finding new “grails,” the slang term used in some cybercrime discussion channels to describe recordings from popular artists that have never been officially released. It stands to reason that King Bob was SIM-swapping important people in the music industry to obtain these files, although there is little to support this conclusion from the public chat records available.
“I got the most music in the com,” King Bob bragged in a Discord server in November 2022. “I got thousands of grails.”
King Bob’s chats show he was particularly enamored of stealing the unreleased works of his favorite artists — Lil Uzi Vert, Playboi Carti, and Juice Wrld. When another Discord user asked if he has Eminem grails, King Bob said he was unsure.
“I have two folders,” King Bob explained. “One with Uzi, Carti, Juicewrld. And then I have ‘every other artist.’ Every other artist is unorganized as fuck and has thousands of random shit.”
King Bob’s posts on Discord show he quickly became a celebrity on Leaked[.]cx, one of most active forums for trading, buying and selling unreleased music from popular artists. The more grails that users share with the Leaked[.]cx community, the more their status and access on the forum grows.
The last cache of Leaked dot cx indexed by the archive.org on Jan. 11, 2024.
And King Bob shared a large number of his purloined tunes with this community. Still others he tried to sell. It’s unclear how many of those sales were ever consummated, but it is not unusual for a prized grail to sell for anywhere from $5,000 to $20,000.
In mid-January 2024, several Leaked[.]cx regulars began complaining that they hadn’t seen King Bob in a while and were really missing his grails. On or around Jan. 11, the same day the Justice Department unsealed the indictment against Urban, Leaked[.]cx started blocking people who were trying to visit the site from the United States.
Days later, frustrated Leaked[.]cx users speculated about what could be the cause of the blockage.
“Probs blocked as part of king bob investigation i think?,” wrote the user “Plsdontarrest.” “Doubt he only hacked US artists/ppl which is why it’s happening in multiple countries.”
FORESHADOWING
On Sept. 21, 2022, KrebsOnSecurity told the story of a “Foreshadow,” the nickname chosen by a Florida teenager who was working for a SIM-swapping crew when he was abducted, beaten and held for a $200,000 ransom. A rival SIM-swapping group claimed that Foreshadow and his associates had robbed them of their fair share of the profits from a recent SIM-swap.
In a video released by his abductors on Telegram, a bloodied, battered Foreshadow was made to say they would kill him unless the ransom was paid.
As I wrote in that story, Foreshadow appears to have served as a “holder” — a term used to describe a low-level member of any SIM-swapping group who agrees to carry out the riskiest and least rewarding role of the crime: Physically keeping and managing the various mobile devices and SIM cards that are used in SIM-swapping scams.
KrebsOnSecurity has since learned that Foreshadow was a holder for a particularly active SIM-swapper who went by “Elijah,” which was another nickname that prosecutors say Urban used.

Shortly after Foreshadow’s hostage video began circulating on Telegram and Discord, multiple known actors in the SIM-swapping space told everyone in the channels to delete any previous messages with Foreshadow, claiming he was fully cooperating with the FBI.
This was not the first time Sosa and his crew were hit with violent attacks from rival SIM-swapping groups. In early 2022, a video surfaced on a popular cybercrime channel purporting to show attackers hurling a brick through a window at an address that matches the spacious and upscale home of Urban’s parents in Sanford, Fl.
“Brickings” are among the “violence-as-a-service” offerings broadly available on many cybercrime channels. SIM-swapping and adjacent cybercrime channels are replete with job offers for in-person assignments and tasks that can be found if one searches for posts titled, “If you live near,” or “IRL job” — short for “in real life” job.
A number of these classified ads are in service of performing brickings, where someone is hired to visit a specific address and toss a brick through the target’s window. Other typical IRL job offers involve tire slashings and even drive-by shootings.
THE COM
Sosa was known to be a top member of the broader cybercriminal community online known as “The Com,” wherein hackers boast loudly about high-profile exploits and hacks that almost invariably begin with social engineering — tricking people over the phone, email or SMS into giving away credentials that allow remote access to corporate internal networks.
Sosa also was active in a particularly destructive group of accomplished criminal SIM-swappers known as “Star Fraud.” Cyberscoop’s AJ Vicens reported last year that individuals within Star Fraud were likely involved in the high-profile Caesars Entertainment an MGM Resorts extortion attacks.
“ALPHV, an established ransomware-as-a-service operation thought to be based in Russia and linked to attacks on dozens of entities, claimed responsibility for Caesars and MGM attacks in a note posted to its website earlier this month,” Vicens wrote. “Experts had said the attacks were the work of a group tracked variously as UNC 3944 or Scattered Spider, which has been described as an affiliate working with ALPHV made up of people in the United States and Britain who excel at social engineering.”
In February 2023, KrebsOnSecurity published data taken from the Telegram channels for Star Fraud and two other SIM-swapping groups showing these crooks focused on SIM-swapping T-Mobile customers, and that they collectively claimed access to T-Mobile on 100 separate occasions over a 7-month period in 2022.
The SIM-swapping groups were able to switch targeted phone numbers to another device on demand because they constantly phished T-Mobile employees into giving up credentials to employee-only tools. In each of those cases the goal was the same: Phish T-Mobile employees for access to internal company tools, and then convert that access into a cybercrime service that could be hired to divert any T-Mobile user’s text messages and phone calls to another device.
Allison Nixon, chief research officer at the New York cybersecurity consultancy Unit 221B, said the increasing brazenness of many Com members is a function of how long it has taken federal authorities to go after guys like Sosa.
“These incidents show what happens when it takes too long for cybercriminals to get arrested,” Nixon said. “If governments fail to prioritize this source of threat, violence originating from the Internet will affect regular people.”
NO FIXED ADDRESS
The Daytona Beach News-Journal reports that Urban was arrested Jan. 9 and his trial is scheduled to begin in the trial term starting March 4 in Jacksonville. The publication said the judge overseeing Urban’s case denied bail because the defendant was a strong flight risk.
At Urban’s arraignment, it emerged that he had no fixed address and had been using an alias to stay at an Airbnb. The judge reportedly said that when a search warrant was executed at Urban’s residence, the defendant was downloading programs to delete computer files.
What’s more, the judge explained, despite telling authorities in May that he would not have any more contact with his co-conspirators and would not engage in cryptocurrency transactions, he did so anyway.
Urban entered a plea of not guilty. Urban’s court-appointed attorney said her client would have no comment at this time.
Prosecutors charged Urban with eight counts of wire fraud, one count of conspiracy to commit wire fraud, and five counts of aggravated identity theft. According to the government, if convicted Urban faces up to 20 years in federal prison on each wire fraud charge. He also faces a minimum mandatory penalty of two years in prison for the aggravated identity offenses, which will run consecutive to any other prison sentence imposed.




Thanks, Krebs! Couldn’t happen to a nicer guy!!
Hitler had friends that loved him. What is it to be ‘nice’?
Wow this happened in the “386” Was he living the life over on beach side?
386 is not near Orlando.
case number is 3:23-cr-00180
https://arstechnica.com/tech-policy/2024/01/sim-swapping-ring-stole-400m-in-crypto-from-a-us-company-officials-allege/
It’s really pathetic how all of these white bread criminals are obsessed with rap music. Wannabe thugs. At least every once in a while one of them does the time.
Kill them all with death kyke bastards
yeah and all the other humans too! myself included of course. fellow human!
It does not make sense that people employed in tech are supplying their credentials .
The phishing texts and sites are a ruse to cover the larger ops of the organized crime aspect of the big G, FB, Hyundai, etc., when the managers of the boiler room operations in Arizona, i.e., the contractors who supply customer service, tech support and sales to big G, FB, Hyundai, reward their insiders with opportunities to sieze assets, because of public perception that big G, FB, Hyundai are trustworthy and regulated. Not.
Always; -Love the great research you do
– disappointed in the lack of punishment given to people that take a lifetime of hard works savings, leaving people destitute.
Which 100% encourages people to be criminals. So much to gain, so little to lose. It’s wrong.
See, I worked 40 years, saved 1/4 of my earning to retire. While if I had been a criminal, stole money and set some aside, went to jail for 2-10 years and come out with more money than working 40 years, and have time to enjoy it…. yeah, guess I’m the fool. Still won’t be a scumbag thief.
What kind of thief one is depends on one’s viewpoint and gross take. Once you get to the level of corporate CEO, as those testifying before the US Congress today, your stealing is looked at differently. While stealing in the hundreds of thousands will get you Big Bubba as your cellie, stealing in the billions presents you as a leader in commerce. Now you are considered a respected businessman rather than a scumbag thief, and people try to emulate you. Why? It’s the same idea as what John Harington said in the 17th century about treason…
I have never considered people like zukerberg, gates, biden, broula, anything other than greedy scumbags. Maybe on TV they kiss their butt, but not in my house.
I’ll wait for the conviction and are least a twenty year sentence for this criminal and all other criminals involved. Since it is multiple crimes involved, then he should get a twenty year sentence for each crime and not be eligible for parole for twenty years. That leniency should only happen if he testifies against all others of all crews. Otherwise he shoukd get max sentences for each crime that need to run consecutively so that he spends 80 years in jail. Until real hard time is handed out to all high tech criminals, we will be inviting high risk. All companies who do not have solid security should be sued in class action law suits until people start taking security seriously.
Intuition is not equivalent to analysis. Please, stop it.
We HAVE to get past sms as a 2fa method. You can’t trust some random, under paid employee not to send criminals your sim card.
On another note, it’s pretty sad that these gangs pay the device and sim holder the least. Your operation is impossible without them and it’s the most risky task. I guess I shouldn’t be surprised that criminals act like scumbags amongst eachother.
IronVest has a sim-swapping solution, as well as YubiKeys
Thanks for sharing this. Looks like a well rounded solution.
“We HAVE to get past sms as a 2fa method.”
And herein lies the problem. Governments needs to start listening to Security Organisations and NOT C-Suite when implementing legislation. SMS/Email for 2FA are just another digital hurdle (some code or social engineering) for bad actors to bypass. Physical 2FA such as hardware keys increase security dramatically but nobody is encouraged to implement it, consumers or corporations alike, for the sake of convenience and the dollar.
If you go to https://2fa.directory and see how many online entities still have ZERO 2FA implementations whatsoever, you’d be gob smacked. The majority listed have some form of digital/software based 2FA as a requirement, but very few offer physical/hardware 2FA as an option.
In my region (not US or EU) for instance, take the ‘Banking’, ‘Payments’ and ‘Cryptocurrencies’ categories as an example. In each, there are 14, 37 and 108 entities listed respectively for a total 159 entities. Of the 14 domestic Banks listed, NONE offer a hardware option and 5 offer NO 2FA at all. Of the 37 Payment services listed just 3 offer a hardware option and 9 have NO 2FA at all. And lastly of the 108 Cryptocurrency exchanges listed only 10 offer hardware options whilst only 3 have NO 2FA at all. THIS IS ABYSMAL
C-Suite says it’s all too hard or expensive to implement. That’s not good enough. Their bottom line or bonuses should not factor into it, it should be compulsory. What about the cost to the community? Financially, Cybercrime only cost my country $3.2billion last financial year, but the World Economic Forum says “the global cost of online criminal acts is expected to surge to $23.84 trillion by 2027, up from $8.44 trillion in 2022, according to data from Statista, the FBI and IMF.”
These figures are staggering and the fact that no one is forced to do anything about it is just beyond me.
Two reasons – Free market (put your money where you want to, even if its stupid) and Profiting from criminal activity by big companies and government – yeah, if it wasn’t for organized crime the FBI/facebook/bitcoin banks wouldn’t be nearly as powerful and underhanded as they are now. The more crime the more powerful they become, so it’s in their interest as a dept to keep crime rates up – job security. add in any 3 letter agency or IT power house (MS) into that. But that’s just my opinion at this moment.
My bank only allows for text based 2fa. Won’t even let me ise my yubico key. Drives me crazy.
Same. I have online bank accounts, but they are never used as I have a branch 10 minutes away if it is really important ie; documents etc, and, they know who I am. Online, I use Paypal as a financial intermediary, because the only way to access that is with a hardware key.
If I’m traveling, particularly overseas, I will use Privacy.com’s virtual credit cards. Book in to a hotel with newly created virtual card. Check out and destroy card. Simple. Any unwanted after charges/fraud go straight down the rabbit hole. Good for those pesky hard to cancel trial/subscription services.
A court-appointed attorney? He was charged with stealing $800,000 in the last seven months.
Did the feds freeze his assets preventing him from hiring his own defense counsel? I hate it when they do that.
IronVest has a sim-swapping solution as well as YubiKey’s
Great article. I still can not believe SIM swapping is happening and that these kids that do it call themselves hackers. Compared to the programmers that write malware or Pegasis they are a joke and have no skills except patience in finding a dumb employee which must not take long.
And the DevOps Employee at Lastpass one of only 4 people to have access to the vault running 2 year old Plex software at home? What a joke.
Also never knew people paid big money for unreleased rap tracks, which 95% must be horrible demos, that were never even mixed or mastered was pretty interesting.
One long walk along the Venice Beach boardwalk in California and you can get all of the unreleased rap tracks you desire.
Noah Michael Urban is NOT member of “Scattered Spider”. This connection is completely artificial. Unless Russians decided to show such attribution 🙂 Hello Sberbank – Vlad is happy.
Curious why after so many high-profile sim swap “success” stories… why is it still so seemingly easy to sim swap?
If you’re saying it should be more difficult overall, absolutely. And less useful.
Because the telcos do not lose money from it, they merely replace the one who got phished with another, and carry on. Till they also are named as a defendant, and have some large fines imposed on them, per swap, big enough to appear in an annual statement per case, they will not care at all.
An even more important question is why most banks still don’t offer Passkeys, ubikeys or authenticator apps as a much more secure type of 2FA than SMS-based 2FA?
I agree yet if they jst sold Crack a couple of times they would be incarcerated to the point of be institutionalized. 100 million stolen = 30 months . Sign me up Rather lose 30 months then entire life just to retire then die making a tenth of that
Where can I find his indictment? Would love to read up on it.
In light of the recent arrest and charges against Noah Michael Urban for his alleged involvement in SIM-swapping and cyber intrusions, what steps do you believe law enforcement and cybersecurity experts should prioritize to address the growing threats posed by sophisticated hacking groups like Oktapus and Scattered Spider?
Additionally, how can authorities effectively collaborate with technology companies and online platforms to prevent and mitigate such cybercrimes in the future?