Threat Model Thursday: Technology Consumers
Adam Shostack
APRIL 29, 2021
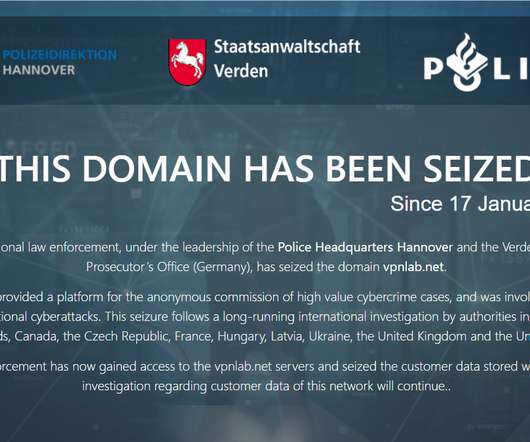
It opens “While many forms of data-driven surveillance are now a ‘fact’ of contemporary life amidst datafication, obtaining concrete knowledge of how different institutions exploit data presents an ongoing challenge, requiring the expertise and power to untangle increasingly complex and opaque technological and institutional arrangements.”

































Let's personalize your content