5 Main Ransomware Attack Vectors in 2023

Ransomware is a sly, silent, and vicious criminal. It quietly makes its way past your security defenses into the heart of your data. It then keeps it hostage until you pay a ransom. To defend against it you need to understand how you get ransomware in the first place. Learn the key ransomware attack vectors in the upcoming 2023.
As cybersecurity experts, we want users to understand how ransomware infects a system and help you to protect your data from it.
In this article, we will take a detailed look at how ransomware makes its way into your network and onto your computer and see how you can defend your data assets!
Ransomware Attack Vectors: Key Points
So, where do you get ransomware from? There are five main ransomware infection methods threat actors use to inject ransomware on your computer.
Many attacks exploit human nature by employing social engineering tactics to deceive users into unknowingly permitting ransomware onto their system, disguised as something legitimate.
Let’s examine the following ransomware attack vectors more closely:
- Ransomware via phishing emails
- Ransomware via exploit kits
- Ransomware via brute force attacks
- Ransomware via malicious apps and extensions
- Ransomware via infected executables
Ransomware via Phishing Emails
Phishing emails have many faces, but what unites them is the seeming legitimacy and a requirement to take action, exposing one of the ransomware vectors.
Let’s take a phishing email that one of our colleagues got some time ago as an example to illustrate the most common signs:

1. “Screaming” subject
In our case, it is “Notice [WARNING],” but it can be anything else that catches your attention. This is a signal because companies like Google never use this kind of subject.
2. Seeming legitimacy
To make the email look legitimate, hackers pretend it to be from Google. Well-known companies like Google, Microsoft, Amazon, Pay Pal, etc. are the widespread choice for hackers because people open them without any hesitation.
But note that it can also pretend to be from someone from your company. This might be your boss, or somebody from HR, IT, or accounting departments.
3. Urge to take action (click or download)
Hackers placed the large button and prompted us to click on it, rushing us to upgrade our system. Sometimes it can be an attachment an email urges you to open or download or sensitive information you need to provide.
When you click on the button or attachment, two things can happen:
- You get redirected to a malicious website that asks you to type in some information. It can be your login and password to your Microsoft 365 or Google Workspace or some other information. Using this information, hackers can get into the system and infect it. The consequences can be catastrophic for organizations that rely all of their day-to-day operations on cloud data.
- You get redirected to a site that asks you to provide some permissions or download something. If you provide permissions, the virus infects the system you gave access to; if you download something, this file spreads ransomware across your computer or cloud.
4. Weird sender address.
By “weird”, we mean an email address that doesn’t match the sender it claims to be from. In our case, the message claims to be from Google, but the sender email looks like this: upgrades@gmail-com.com Obviously, the address is fake because it contains two words “com,” one of which is hyphenated.
Even for those who don’t know that Google never offers to update your system via email, this address would look suspicious.
5. Spoofed website URL
To see whether the site the email is sending you to is legitimate, you have to hover over the link before visiting it. If the site is fake, it will have a misspelling in it; sometimes, the address can be completely unrelated to what it pretends to be.
Examples:
- The link looks like this www.amazoon.com instead of www.amazon.com (misspelling)
- The link looks legitimate at first glance, but when you hover over it, it shows gibberish. Like this: www.bankofamerica.com → www. bit.do/kjbsiudb.
In our screenshot example, you can’t hover over the link that the email pushes us to click because it’s a button. So you should be careful and look for other signs we list here.
One of the worst consequences that can happen via phishing emails is lateral movement.
What is Lateral Movement?
Lateral movement is when an attacker “stays law” in the system to broaden the infection zone by trying to access other services. Instead of making itself known by encrypting files and displaying a ransom note, ransomware quietly stays in your system and scans the network for other vulnerabilities.
Ransomware can stay in your system for months, collecting information that will help it to spread across other computers. It uses an internal scanning to find other machines inside the network and the ways to infect them.
As mentioned earlier, if your company uses Microsoft 365 or Google Workspace, the consequences of even one such infection can be catastrophic. By using lateral movement, ransomware can silently spread across the public cloud and encrypt files of the whole organization.
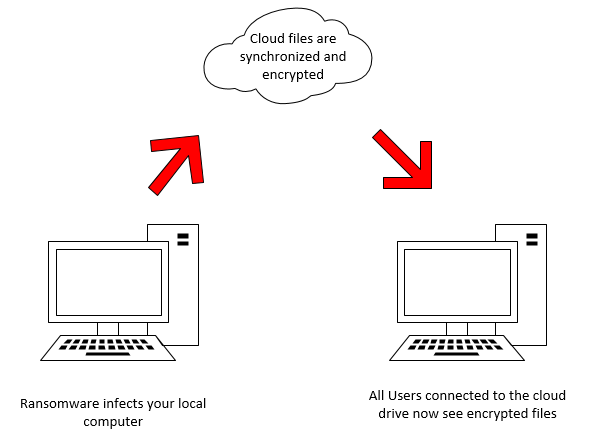
This “Ransomcloud” attack, as demonstrated by Kevin Mitnick, then runs a malicious script that actively encrypts your cloud email inbox.
The ransomware can also search for and encrypt files on any network drives and mapped drives that you are connected to.
Keep in mind that locally synchronized files such as Microsoft’s OneDrive or Google Drive/Backup and Sync files will generally be encrypted as well.
Ransomware via Exploit Kits
Exploit is a vulnerability in a system or network that allows using it for malicious goals. One of the most famous examples is the EternalBlue exploit, which was the main channel of the WannaCry ransomware attack in 2017.
An exploit kit is a bunch of different exploits gathered together on one management platform to make it easier for attackers to use them.
Exploit kits can infect you via so-called “malvertising” – a fake ad or pop-up, that can appear on even legitimate websites.
Malvertising example
What do exploit kits do?
They scan and find vulnerabilities in the software you are running. This could include exploits related to your browser, operating system, or plugins like Java or Flash.
Once a known exploit is found, the exploit kit can then capitalize on the vulnerability and inject ransomware code in your system.
The steps in the process include the following:
Step 1
You visit a legitimate (or seemingly legitimate) website that has an injected malicious code in it that looks like advertising.
Step 2
You click on this ad. It redirects you to a malicious site, although it may look legitimate, and it starts scanning your system for vulnerabilities or outdated software.
Step 3
Once the malware has found a vulnerability, the exploit kit will inject a malicious code there and download ransomware on your system. It encrypts your files and displays a typical ransom note.
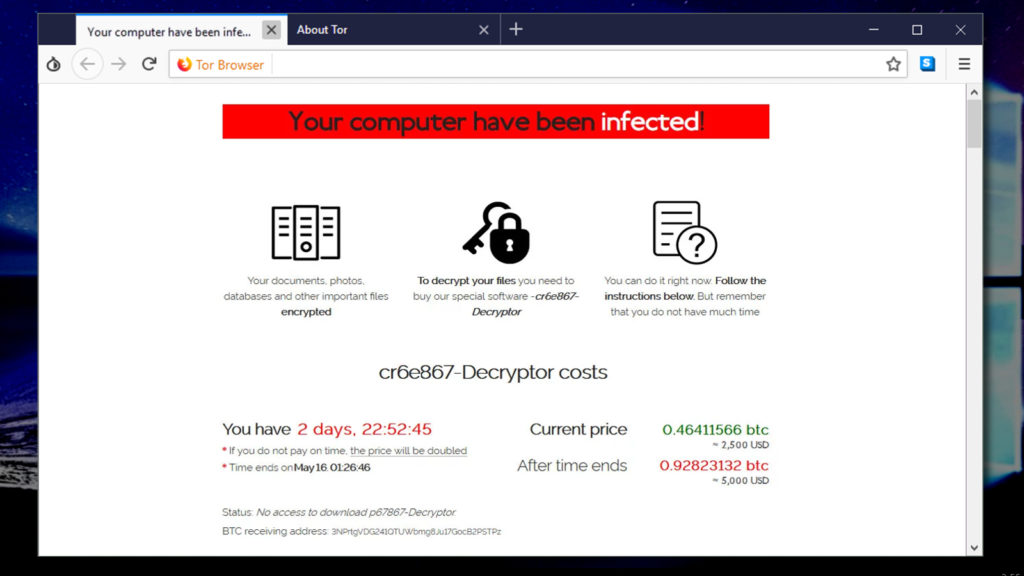
Sodinokibi ransomware note
How to protect from exploit kits:
Run only up-to-date software. Avoid using old versions of operating systems because tech companies don’t make security updates for such versions. And those security updates are vital because they respond to the newly appeared variants of malware and exploits they can use.
Ransomware via Brute Force Attacks
Researchers at F-Secure have found that in 2019, brute force attacks became one of the most preferred means of spreading ransomware.
A brute force attack is a method of gaining access to a site or server by cracking a victim’s password and/or username. To do that, a hacker tries as many passwords as possible, using special software.
The probability and time of cracking vary depending on the length and complexity of a password and can take from a few seconds to a few years. In 81% of cases, the passwords people use are weak and easily crackable.
As IBM reports, some hackers can target the same systems every single day for months or even years.
How does ransomware get on your computer via a brute force attack?
Very simple: when a hacker gains credentials to your Google Workspace or O365 account, they can easily inject malicious code in the environment. For example, they can send you a phishing email, open it, and it will spread across all your files, including shared ones. And if someone you shared files with downloads these files on their computer, they may get infected as well, creating a chain infection.
How to protect from brute force attacks?
There are three must-follow rules:
1. Having a mandatory password policy. It includes the following:
- Uniqueness. The password to your company’s Microsoft 365 mustn’t repeat passwords to other websites;
- Length. Passwords should consist of eight characters or more;
- Variety. The password should include uppercase and lowercase letters plus digits.
- Сomplexity. Never use obvious combinations like “password,” “asdqwe123,” “123456”, “abcdefg,” “1111111.” Adding some digits or letters to these basic combinations won’t make a big difference, maximum will add a few minutes or hours for cracking mechanisms to get the job done.
- Renewability. Change passwords once (better – twice) a year.
2. Enabling multi-factor authentication. It provides one more layer of protection by requiring not only to enter a password but also answer a call or type in digits a user receives in an SMS. So even if hackers crack a password, they need to pass another security layer to get into the system.
3. Use cybersecurity services to detect an attempt to break into your system. This is a necessary option for organizations since it is hard to keep track of whether all users follow the passwords policy and have enabled multi-factor authentication.
SpinRDR provides full protection from brute force attacks, notifying you about each case when cybercriminals make attempts to break into your Google Workspace account. This helps to prevent hackers from breaking into your organization and damaging business data.
Also, SpinOne identifies abnormal login to your cloud account from an unexpected location where you or your employees have never been.
Ransomware via 3rd-Party Applications & Extensions
The method of infecting a device via apps and extensions is now widely used and targets both individual and corporate users. Fake applications are used for many different kinds of scams, including the spreading of ransomware.
Malicious Apps statistic for 2019:
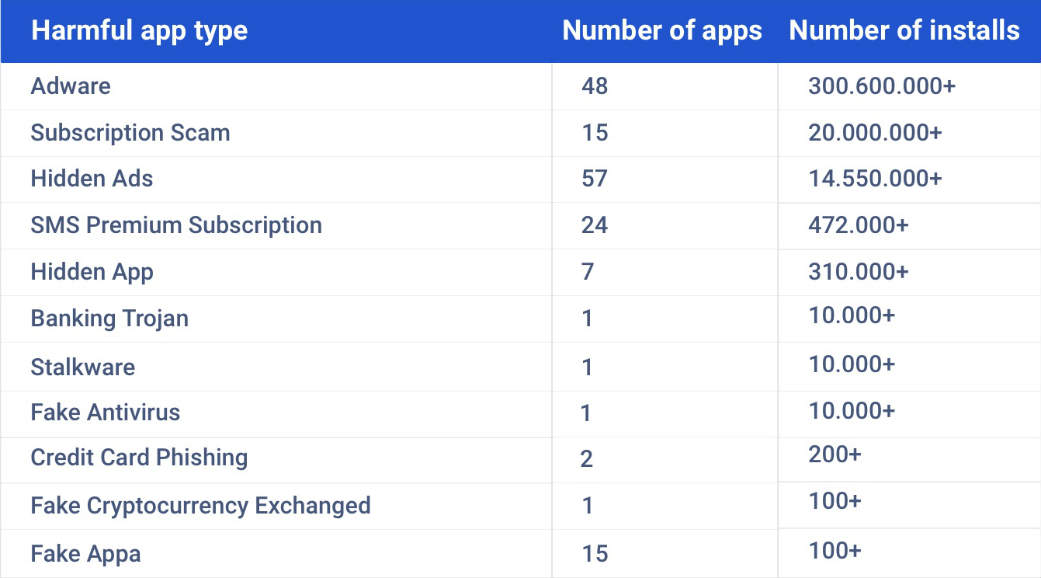
As you can see, Google Workspace Marketplace has become a place where useful applications coexist with tons of fake malicious apps. Some of those fake apps steal your banking data when you try to pay for the extra functionality; others display adware or take money for scam subscriptions. And there are those that infect you with ransomware?
Let’s take a closer look at the common ransomware extensions used for delivering ransomware.
How is ransomware delivered via apps and extensions?
When you install an application or set up an extension, it requests different kinds of permissions. For example, a photo editing application will ask permission to access your photo gallery or your Google Photo folder, etc.
When you choose to provide access, ransomware gets the “green light” and can insert malicious code and encrypt data in the folder you gave access to.
In the corporate cloud environment, the volume of potential damage increases exponentially. If one employee downloaded some fake productivity app and provided it with access to a shared folder, ransomware will infect all files in this folder.
How to avoid malicious apps?
It is almost impossible to distinguish between a malicious and harmless application. Creators make fake apps look exactly like the legitimate ones, buying the reviews, and winding up ratings.
Also, threat actors make apps and extensions look attractive by making them free and promising the abundance of features.
There are three steps you have to take to secure yourself and your organization from malicious apps:
1. Create a must-follow policy about using work devices outside of work. Employees shouldn’t provide access to applications or extensions that are not included in the whitelist. Also, they shouldn’t use these devices for personal purposes, because it increases the risk of catching ransomware while surfing the internet.
If you don’t provide work devices, then this rule should apply to work accounts – employees shouldn’t install any apps or extensions and provide them access using work accounts.
3. Use a risky apps monitoring service or a firewall for blocking suspicious apps. This is the safest and easiest way. Even though whitelist apps policies decrease the risk of being infected, they don’t eliminate it completely. The apps monitoring service lets you keep track of every permission employees grant to apps.
SpinSPM app monitoring service scans 3rd-party apps daily. The service automatically identifies and blocks all risky business apps that request access to your critical Google Workspace data.
Ransomware via Infected Executables
While this infecting point is more a legacy than an actual threat, it still can happen. Therefore, it would be a mistake not to mention the potential risk of infected executables spreading malicious software.
What are Infected Executables?
- Questionable download sites. They host “driver updates” and other supposedly beneficial software that are risky sources of software installations. The process of getting ransomware here is very similar to malicious SPAM links.
- USB drives. Simply plugging an infected USB drive into your computer may begin the encryption process.
5 Rules to Protect Your Data From Ransomware
As you’ve probably heard, the best way to fight ransomware is to prevent it.
Here are the five binding rules which will secure your valuable data from ransomware:
1. Back up data regularly. This rule has no way around it. Companies lose money, customers, and trust every single day because they didn’t have a data protection policy, which includes regular every-day backup.
2. Be attentive and think twice before you click. Memorize all the signs of a phishing email and share this article with your employees so they also could be fully prepared and not fall for a hackers’ bait. Better – print the list of the signs and keep it on your desk.
3. Never visit and download software or files from questionable sites. Use licensed software – in the end, it is much cheaper than dealing with the consequences of downloading free stuff from suspicious websites.
4. Use strong passwords and enable multi-factor authentication. This will decrease your chances to get brute force attacked and infected through the stolen credentials.
5. Use 3rd-party apps monitoring. It is especially vital for organizations that use Google Workspace and need to extend its functionality by installing extensions or applications. Create a whitelist of apps and extensions and don’t go beyond that. Also, you can use special services for monitoring.
If you need an all-in-one service that will cover all the bases, use the cybersecurity service SpinOne and protect your cloud data from ransomware!
Frequently Asked Questions
What are the 2023 top ransomware attack vectors?
According to Sophos The State of Ransomware 2023 Report, the top 2023 ransomware attack vectors include:
- Exploited vulnerability – 36%
- Compromised credentials – 29%
- Malicious email – 18%
- Phishing – 13%
- Brute force attacks – 3%
How often does ransomware encrypt data?
Adversaries succeed in encrypting data in 76% of ransomware attacks, according to Sophos The State of Ransomware 2023 Report. The encryption levels are now at their highest point in the last four years.
What are the most common methods to recover data after a ransomware attack and how effective are they?
The two predominant strategies for data recovery after a ransomware attack are:
- Using backups: Approximately 70% of affected organizations successfully restore their data using backups.
- Paying the ransom: About 46% of organizations resort to paying the ransom to regain access to their data.
A significant 97% of organizations that had their data encrypted managed to recover it, as per findings from the Sophos The State of Ransomware 2023 Report.
What is the mean cost to recover from ransomware in 2023?
The approximate cost to rectify the impacts of the ransomware attack (considering downtime, people time, device cost, network cost, lost opportunity) is 1.82M
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
How to Restore A Backup From Google Drive: A Step-by-Step Guide
April 10, 2024Backing up your Google Drive is like making a safety net for the digital part... Read more
Protecting Partner Margins: An Inside Look at the New Spin.AI Partn...
April 2, 2024Google recently announced a 40% reduction in the partner margin for Google Workspace renewals –... Read more
Expert Insights: SaaS Application Data Protection Fundamentals
March 21, 2024SaaS applications appeal to organizations because they make running the application “somebody else’s problem.” However,... Read more


