Home » Security Bloggers Network » The NIST Pyramid Approach for Small Business
The NIST Pyramid Approach for Small Business
The NIST Pyramid Approach for Small Business
The NIST Pyramid Approach for Small Business
Small businesses lack the wherewithal for fine dining when it comes to IT and cybersecurity spending. We’re wise in the way that we spend our money, and, so, we eat at the local takeout restaurant, using what’s remaining in our wallets to build and grow the business. Yet we’re careful, for if our diet becomes too unhealthy, it often leads to degeneration and disease affecting our business in the long run.
One way for a business to stay healthy is to adopt best practices for cybersecurity. This post is all about preventing the network arteries of your IT ecosystem from clogging up, leading to the failure of critical devices that could diminish the operational efficiency of the business. Like the US food pyramid, cybersecurity requires a balance across groups, and the NIST pyramid can provide that guidance to strike the right balance.
The NIST Cybersecurity Framework (“NIST CF”) is intended to help organizations of all sizes manage and recover from cyber risks and threats as quickly as possible. NIST was developed by the US National Institute of Standards and Technology (NIST). According to a recent survey, approximately 70% of organizations and businesses view the NIST cybersecurity framework as the best approach to prevent, detect, and respond to cyber-attacks.
NIST is a standard rather than a regulation, so compliance is not mandatory for public or private organizations . There are no penalties or fees for non-compliance with NIST. NIST is considered a best-practice standard and it’s wise to try to adopt this standard at your company. Recent studies concluded that large organizations could reduce security risk by 43% while smaller organizations successfully reduced it to 73% using the NIST CF.
Not implementing NIST could mean that your organization is susceptible to a cyberbreach. As of 2022, the average cost of a data breach in the United States amounted to 9.44 million U.S. dollars, up from 9.05 million U.S. dollars in the previous year. The global average cost per data breach was 4.35 million U.S. dollars in 2022. – which is much higher than the cost of implementing the NIST CF.
The NIST cybersecurity framework is comprised of several components: the Core which are the functions to implement the framework: Identify, Protect, Detect, Respond, and Recover. Below the core are 23 categories and a total of 108 sub-categories. The details of the ‘Information Reference’ can be downloaded from here.
Implementation tiers that follow the Core guide organizations on how to assess cybersecurity and manage risk. They address budget and the company’s tolerance for risk. The last component is Framework Profiles to align the organization’s objective, risk appetite, internal requirements, and resources with the outcomes of the framework core.
The key is to maintain a healthy diet across the core and categories, and it all begins with an understanding of the Cyber Protection Pyramid:
Small businesses lack the wherewithal for fine dining when it comes to IT and cybersecurity spending. We’re wise in the way that we spend our money, and, so, we eat at the local takeout restaurant, using what’s remaining in our wallets to build and grow the business. Yet we’re careful, for if our diet becomes too unhealthy, it often leads to degeneration and disease affecting our business in the long run.
One way for a business to stay healthy is to adopt best practices for cybersecurity. This post is all about preventing the network arteries of your IT ecosystem from clogging up, leading to the failure of critical devices that could diminish the operational efficiency of the business. Like the US food pyramid, cybersecurity requires a balance across groups, and the NIST pyramid can provide that guidance to strike the right balance.
The NIST Cybersecurity Framework (“NIST CF”) is intended to help organizations of all sizes manage and recover from cyber risks and threats as quickly as possible. NIST was developed by the US National Institute of Standards and Technology (NIST). According to a recent survey, approximately 70% of organizations and businesses view the NIST cybersecurity framework as the best approach to prevent, detect, and respond to cyber-attacks.
NIST is a standard rather than a regulation, so compliance is not mandatory for public or private organizations . There are no penalties or fees for non-compliance with NIST. NIST is considered a best-practice standard and it’s wise to try to adopt this standard at your company. Recent studies concluded that large organizations could reduce security risk by 43% while smaller organizations successfully reduced it to 73% using the NIST CF.
Not implementing NIST could mean that your organization is susceptible to a cyberbreach. As of 2022, the average cost of a data breach in the United States amounted to 9.44 million U.S. dollars, up from 9.05 million U.S. dollars in the previous year. The global average cost per data breach was 4.35 million U.S. dollars in 2022. – which is much higher than the cost of implementing the NIST CF.
The NIST cybersecurity framework is comprised of several components: the Core which are the functions to implement the framework: Identify, Protect, Detect, Respond, and Recover. Below the core are 23 categories and a total of 108 sub-categories. The details of the ‘Information Reference’ can be downloaded from here.
Implementation tiers that follow the Core guide organizations on how to assess cybersecurity and manage risk. They address budget and the company’s tolerance for risk. The last component is Framework Profiles to align the organization’s objective, risk appetite, internal requirements, and resources with the outcomes of the framework core.
The key is to maintain a healthy diet across the core and categories, and it all begins with an understanding of the Cyber Protection Pyramid:
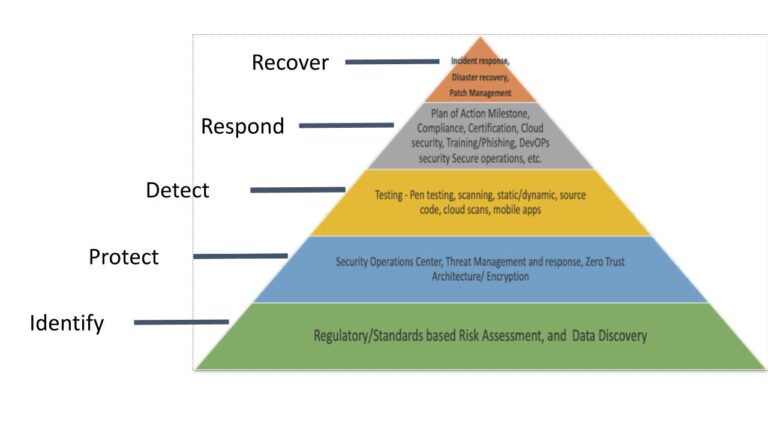
In the Identify phase, the goal is to develop the organizational understanding of cybersecurity risks to systems, assets, data, and capabilities using relevant standards and data discovery. Just as with the food groups in a food pyramid, you will want to spend the most time here.
In level two (Protect), you develop and implement appropriate activities to protect from cyber security events. A Security Operations Center is implemented. Threat Management and Response approaches are defined. A Zero Trust Architecture establishes rules for how and who can access data focusing on providing only what the person needs to do their job. Encryption technologies are deployed to secure data.
The third level Testing Phase involves penetration testing and vulnerability scans of all cloud and mobile apps. For SaaS companies, source code reviews are performed to catch security bugs early in the process rather than later.
Level four (Respond) includes reaching a Plan of Action Milestone and gaining compliance certification. There is a focus on cloud security, cybersecurity awareness, and phishing training. Employee training needs to provide the right level for each user group. Lack of security awareness across the org and lack of employee training allows malware to gleefully gain toeholds into the system. For SaaS companies, DevOps are reviewed.
Identify, Protect, Detect, and Respond help ensure the uncongested flow of network packets through the veins and arteries of your system – the packets that comprise the lifeblood of your business. A healthy blend of the bottom four layers will result in needing to spend less time recovering from a security event and implementing disaster recovery procedures.
Recovery is like the fats, oils, salts, and sugars of a diet—a.k.a. the heart of comfort foods. Here is where the rubber meets the road in your planning: you would need to implement the appropriate activities for resilience to restore any capabilities or services that were impaired due to a security event. Recovery might include applying software patches for known threat vectors. The better prepared you are from the lower four tiers, the easier your recovery process will be.
We hope we have communicated the importance of healthy eating of the NIST Pyramid of cybersecurity activities when it comes to keeping IT ecosystems humming while carrying the load of your business.
SecureFLO will provide a custom solution for your organization to attain compliance with the NIST Cybersecurity Framework. This may include assessment, documentation, process improvement, policy development and training your staff. SecureFLO will support your organization’s growth and development and keep you informed about emerging trends and technologies in the cybersecurity space.
To learn more about the components of the NIST Cybersecurity Framework this link can be followed (here).
Additional supporting material relating to the core functions of the NIST Cybersecurity Framework can be found here.
In the Identify phase, the goal is to develop the organizational understanding of cybersecurity risks to systems, assets, data, and capabilities using relevant standards and data discovery. Just as with the food groups in a food pyramid, you will want to spend the most time here.
In level two (Protect), you develop and implement appropriate activities to protect from cyber security events. A Security Operations Center is implemented. Threat Management and Response approaches are defined. A Zero Trust Architecture establishes rules for how and who can access data focusing on providing only what the person needs to do their job. Encryption technologies are deployed to secure data.
The third level Testing Phase involves penetration testing and vulnerability scans of all cloud and mobile apps. For SaaS companies, source code reviews are performed to catch security bugs early in the process rather than later.
Level four (Respond) includes reaching a Plan of Action Milestone and gaining compliance certification. There is a focus on cloud security, cybersecurity awareness, and phishing training. Employee training needs to provide the right level for each user group. Lack of security awareness across the org and lack of employee training allows malware to gleefully gain toeholds into the system. For SaaS companies, DevOps are reviewed.
Identify, Protect, Detect, and Respond help ensure the uncongested flow of network packets through the veins and arteries of your system – the packets that comprise the lifeblood of your business. A healthy blend of the bottom four layers will result in needing to spend less time recovering from a security event and implementing disaster recovery procedures.
Recovery is like the fats, oils, salts, and sugars of a diet—a.k.a. the heart of comfort foods. Here is where the rubber meets the road in your planning: you would need to implement the appropriate activities for resilience to restore any capabilities or services that were impaired due to a security event. Recovery might include applying software patches for known threat vectors. The better prepared you are from the lower four tiers, the easier your recovery process will be.
We hope we have communicated the importance of healthy eating of the NIST Pyramid of cybersecurity activities when it comes to keeping IT ecosystems humming while carrying the load of your business.
SecureFLO will provide a custom solution for your organization to attain compliance with the NIST Cybersecurity Framework. This may include assessment, documentation, process improvement, policy development and training your staff. SecureFLO will support your organization’s growth and development and keep you informed about emerging trends and technologies in the cybersecurity space.
To learn more about the components of the NIST Cybersecurity Framework this link can be followed (here).
Additional supporting material relating to the core functions of the NIST Cybersecurity Framework can be found here.
The post The NIST Pyramid Approach for Small Business first appeared on SecureFLO.
*** This is a Security Bloggers Network syndicated blog from SecureFLO authored by service. Read the original post at: https://secureflo.net/blog/the-nist-pyramid-approach-for-small-business/





