VoltSchemer attacks use wireless chargers to inject voice commands, fry phones
Bleeping Computer
FEBRUARY 20, 2024
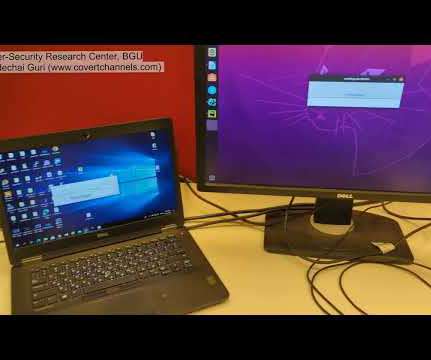
A team of academic researchers show that a new set of attacks called 'VoltSchemer' can inject voice commands to manipulate a smartphone's voice assistant through the magnetic field emitted by an off-the-shelf wireless charger. [.]















































Let's personalize your content