Contents:
Moshen Dragon is a strong hacking organization that has the capacity to change its strategy based on the kind of defenses they are encountering. When it comes to sideloading malicious Windows DLLs into antivirus programs, stealing passwords to move laterally, and finally exfiltrating data from affected PCs, the hackers are quite persistent.
What Happened?
In Central Asia, researchers from Sentinel Labs have discovered a new cluster of hostile cyber activity that has been labeled Moshen Dragon and that is targeting communications service providers.
While there are some similarities between this new threat organization and “RedFoxtrot” and “Nomad Panda,” such as the employment of ShadowPad and PlugX malware variants, there are enough distinctions in their activities to keep them apart from one another in terms of activity.
Due to the lack of knowledge about the infection vector at this time, Sentinel Lab’s analysis starts with an examination of antivirus misuse, which covers products from TrendMicro, Bitdefender, McAfee, Symantec, and Kaspersky as well as others.
Usually, good detection has an inverse relationship with visibility of a threat actor’s TTPs. When part of an infection chain gets detected, it usually means that we don’t get to see what the threat actor intended to deploy or ultimately do. In an unexpected twist, our detection capabilities uncovered an unusual TTP as Moshen Dragon attempted to repeatedly bypass that detection.
Every time the intended payload was blocked, we were able to witness the actor’s reliance on a wide variety of legitimate software leveraged to sideload ShadowPad and PlugX variants. Many of these hijacked programs belong to security vendors, including Symantec, TrendMicro, BitDefender, McAfee and Kaspersky.
Rather than criticize any of these products for their abuse by an insistent threat actor, we remind readers that this attack vector reflects an age-old design flaw in the Windows Operating System that allows DLL search order hijacking. Tracking of additional Moshen Dragon loading mechanisms and hijacked software surfaced more payloads uploaded to VirusTotal, some of which were recently published under the name ‘Talisman’.
Side-loading a malicious DLL onto these antivirus products’ processes, which operate with high privileges on the Windows operating system, allows the hackers to execute the malware on the computer with little constraints, possibly evading detection and detection.
As BleepingComputer reported, a Python kit designed to assist lateral movement and remote code execution through Windows Management Instrumentation (WMI) is deployed using this way by Moshen Dragon (WMI).
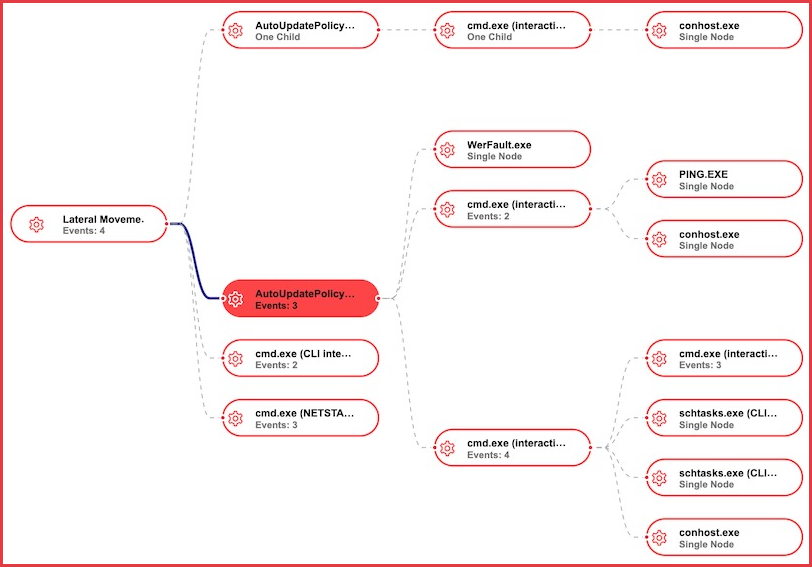
As a bonus, Impacket incorporates an open-source application that collects the details of password change events on a domain and writes them to the “C:WindowsTempFilter.log” file, which is located in the “C:WindowsTempFilter.log” directory.
Knowing that the threat group has access to their computers, the group installs a passive loader on them that checks the hostname against a hardcoded number to ensure that it is on the correct machine before launching the malware.
How Can Heimdal™ Help?
Threats at the domain level represent the new normal nowadays. That is why an efficient cloud-based security solution is the answer to this problem. Try out our awarded Threat Prevention, an outstanding DNS traffic filtering that has found the perfect way to mix together ingredients like Machine Learning, cybercrime intelligence, and AI-based prevention into a perfect cybersecurity recipe that safeguards your business-critical assets from DNS threats with an accuracy of 96%. No time to get hacked as you are busy taking threat hunting to the next level!
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










