TheMoon” Malware Returns: Thousands of Routers Compromised
Penetration Testing
MARCH 26, 2024
Researchers at Lumen Technologies’ Black Lotus Labs have uncovered a newly updated version of the “TheMoon” malware, dating back to 2014.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Penetration Testing
MARCH 26, 2024
Researchers at Lumen Technologies’ Black Lotus Labs have uncovered a newly updated version of the “TheMoon” malware, dating back to 2014.
Security Affairs
DECEMBER 26, 2023
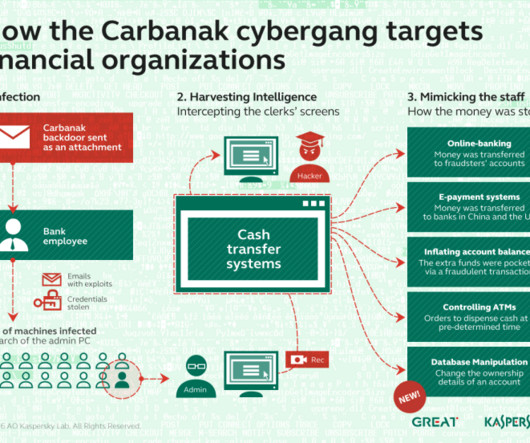
Researchers at NCC Group reported that in November they observed the return of the infamous banking malware Carbanak in ransomware attacks. The cybersecurity firm NCC Group reported that in November the banking malware Carbanak was observed in ransomware attacks. ” reads the report published by NCC Group.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
NOVEMBER 25, 2020
million settlement in a multi-state investigation of the data breach that the company suffered in 2014. million settlement over the 2014 data breach. In 2014, Home Depot revealed that the data breach impacted 56 million customers across the US and Canada. Retail giant Home Depot has agreed to a $17.5 ” . .

Krebs on Security
JUNE 21, 2023
If you operate a cybercrime business that relies on disseminating malicious software, you probably also spend a good deal of time trying to disguise or “crypt” your malware so that it appears benign to antivirus and security products. This story explores the history and identity behind Cryptor[.]biz WHO RUNS CRYPTOR[.]BIZ?

Penetration Testing
DECEMBER 27, 2023
According to the monthly threat analysis by NCC Group, the banking malware Carbanak, known since 2014, has updated its methods and is now actively used in ransomware attacks.

Krebs on Security
JUNE 1, 2023
This post is a deep dive on “ Megatraffer ,” a veteran Russian hacker who has practically cornered the underground market for malware focused code-signing certificates since 2015. More recently, it appears Megatraffer has been working with ransomware groups to help improve the stealth of their malware. WHO IS MEGATRAFFER?

Schneier on Security
NOVEMBER 24, 2023
The group—known by many names, including Gamaredon, Primitive Bear, ACTINIUM, Armageddon, and Shuckworm—has been active since at least 2014 and has been attributed to Russia’s Federal Security Service by the Security Service of Ukraine. A new worm that spreads via USB sticks is infecting computers in Ukraine and beyond.

Schneier on Security
AUGUST 18, 2020
Interesting story of a vaccine for the Emotet malware: Through trial and error and thanks to subsequent Emotet updates that refined how the new persistence mechanism worked, Quinn was able to put together a tiny PowerShell script that exploited the registry key mechanism to crash Emotet itself.

Schneier on Security
OCTOBER 10, 2019
Kaspersky has a detailed blog post about a new piece of sophisticated malware that it's calling Reductor. Based on these similarities, we're quite sure the new malware was developed by the COMPfun authors. The COMpfun malware was initially documented by G-DATA in 2014.

Security Affairs
FEBRUARY 17, 2024
Ukrainian national Vyacheslav Igorevich Penchukov has pleaded guilty to his key roles in the Zeus and IcedID malware operations. Vyacheslav Igorevich Penchukov was a leader of two prolific malware groups that infected thousands of computers with malicious software. Since May 2019, Penchukov had a prominent role in the Zeus operation.

Krebs on Security
APRIL 18, 2023
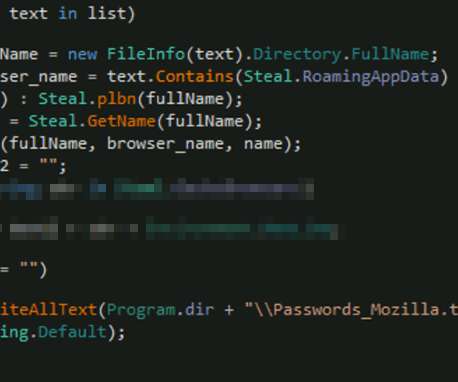
For the past seven years, a malware-based proxy service known as “ Faceless ” has sold anonymity to countless cybercriminals. The proxy lookup page inside the malware-based anonymity service Faceless. Image: spur.us. as a media sharing device on a local network that was somehow exposed to the Internet.
Security Affairs
AUGUST 27, 2020
Microsoft warned of a recently uncovered piece of malware, tracked as Anubis that was designed to steal information from infected systems. This week, Microsoft warned of a recently uncovered piece of malware, tracked as Anubis, that was distributed in the wild to steal information from infected systems. Pierluigi Paganini.
The Hacker News
MAY 20, 2022
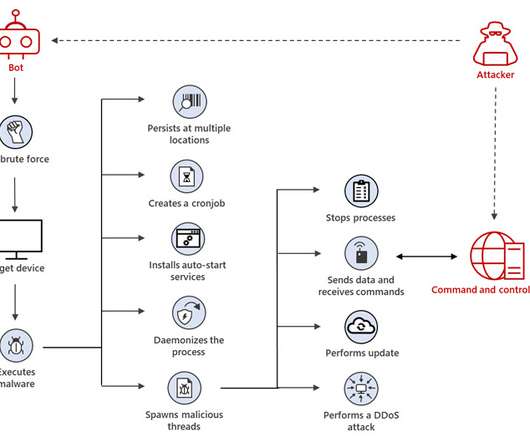
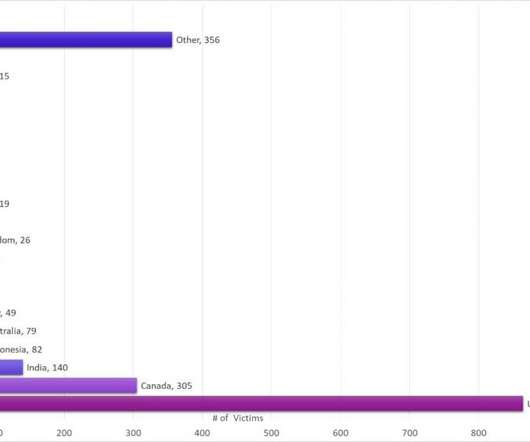
A Linux botnet malware known as XorDdos has witnessed a 254% surge in activity over the last six months, according to latest research from Microsoft. XorDdos' modular
Security Affairs
JANUARY 10, 2022
A malware campaign spreads ZLoader malware by exploiting a Windows vulnerability that was fixed in 2013 but in 2014 Microsoft revised the fix. Experts from Check Point Research uncovered a new ZLoader malware campaign in early November 2021. banking Trojan and was used to spread Zeus-like banking trojan (i.e.
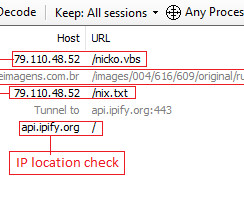
Security Affairs
DECEMBER 21, 2023
Threat actors are exploiting an old Microsoft Office vulnerability, tracked as CVE-2017-11882, to spread the Agent Tesla malware. Threat actors are exploiting an old Microsoft Office vulnerability, tracked as CVE-2017-11882 (CVSS score: 7.8), as part of phishing campaigns to spread the Agent Tesla malware.
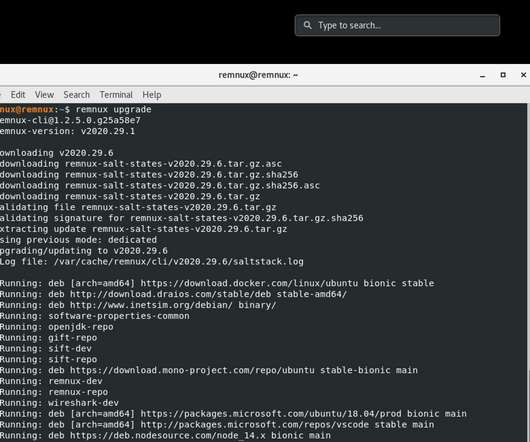
Security Affairs
JULY 26, 2020
A new version of the REMnux Linux toolkit for malware analysts is available for download, it includes a huge set of tools for professionals. REMnux is a Linux toolkit for reverse-engineering and dissecting software, it includes a collection of free tools created by the community that allows researchers to investigate malware.

CSO Magazine
JANUARY 20, 2022
It was thought the malware, first discovered in 2014, had been vanquished by law enforcement agencies from eight countries in January 2021. “Emotet has been one of the most professional and long-lasting cybercrime services out there,” according to Europol. However, it reportedly resurfaced this past November.

Security Affairs
SEPTEMBER 16, 2020
A threat actor is launching brute-force attacks on MSSQL servers in the attempt to access them to install a new crypto-mining malware dubbed MrbMiner. A group of hackers is launching brute-force attacks on MSSQL servers with the intent to compromise them and install crypto-mining malware dubbed MrbMiner. Mining process.”
Security Affairs
MARCH 12, 2020
Cybercriminals continue to exploit the fear in the coronavirus outbreak to spread malware and steal sensitive data from victims. Experts from cybersecurity Reason reported cybercrimnals are using new coronavirus -themed attacks to deliver malware. To make sure the malware can persist and keep operating, it uses the “Task Scheduler”.”
Security Affairs
OCTOBER 25, 2020
Researchers from MalwareHunterTeam have spotted a new piece of remote access trojan (RAT) dubbed ‘Abaddon’ that is likely the first malware using the Discord platform as command and control. The Abaddon malware connects to the Discord command and control server to check for new commands to execute. "Abaddon"
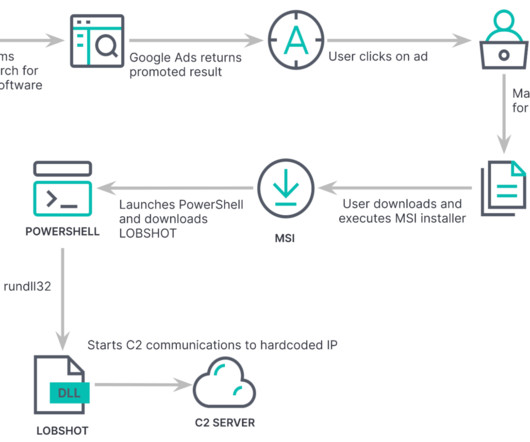
Security Affairs
MAY 1, 2023
The previously undetected LOBSHOT malware is distributed using Google ads and gives operators VNC access to Windows devices. Threat actors are using an elaborate scheme of fake websites through Google Ads to spread their malware, the backdoors are embedded in installers for apparently legitimate applications, such as AnyDesk.

Security Affairs
MAY 13, 2020
The United States Cyber Command (USCYBERCOM) has uploaded five new North Korean malware samples to VirusTotal. The United States Cyber Command (USCYBERCOM) has shared five new malware samples attributed to the North Korea-linked Lazarus APT , it has uploaded the malicious code to VirusTotal. ” reads the DHS CISA’s advisory.

Malwarebytes
MAY 25, 2022
XorDDoS, a Linux Trojan known for its modularity and stealth, was first discovered in 2014 by the white hat research group, MalwareMustDie (MMD). Based on a case study in 2015 , Akamai strengthened the theory that the malware may be of Asian origin based on its targets. MMD believed the Linux Trojan originated in China.
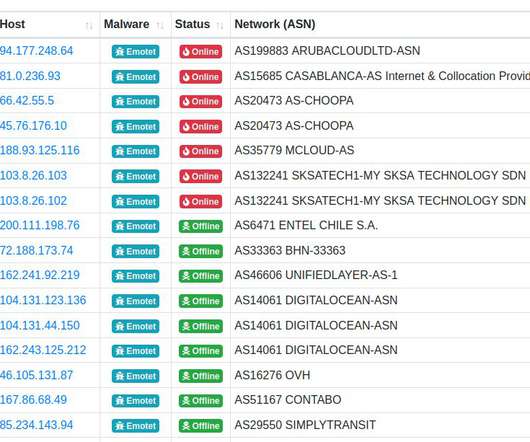
Security Affairs
NOVEMBER 15, 2021
The FBI collected millions of email addresses used by Emotet operators in their malware campaigns as part of the cleanup operation. The Emotet banking trojan has been active at least since 2014, the botnet is operated by a threat actor tracked as TA542. Malware tracking non-profit organization Abuse.ch ” reported GData.
Security Affairs
NOVEMBER 22, 2020
Two Romanians arrested for running three malware services. Two Romanians have been arrested for running two malware crypter services called CyberSeal and DataProtector, and the CyberScan malware testing service. The post Romanians arrested for running underground malware services appeared first on Security Affairs.
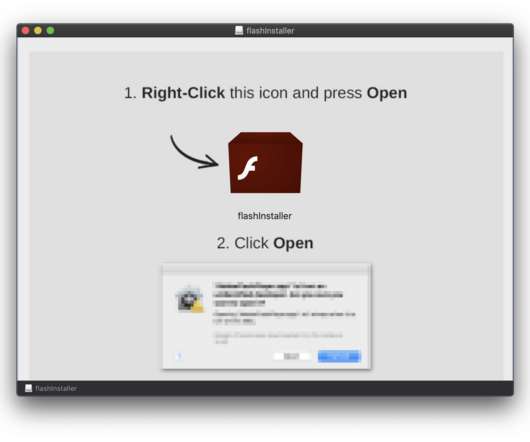
Security Affairs
JUNE 21, 2020
Shlayer Mac malware is back, the Mac threat is now spreading through new black SEO operations. Researchers spotted a new version of the Shlayer Mac malware that is spreading via poisoned Google search results. The malware can be used to download other malicious payloads, including malware or adware. up to 10.14.3.
Security Affairs
OCTOBER 19, 2020
Researchers from Kaspersky Lab have spotted new variants of the GravityRAT malware that now can be also used to infect Android and macOS devices. GravityRAT is a malware strain known for checking the CPU temperature of Windows computers to avoid being executed in sandboxes and virtual machines. Pierluigi Paganini.
Security Affairs
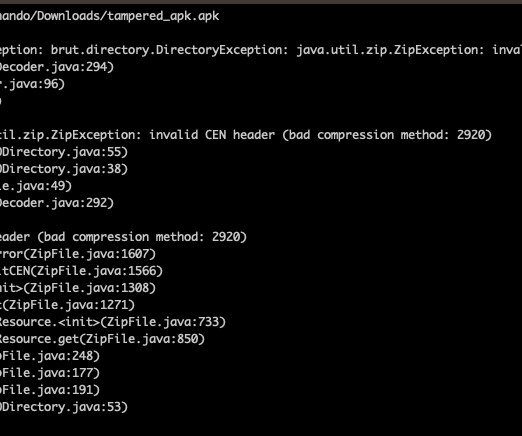
AUGUST 19, 2023
Threat actors are using Android Package (APK) files with unsupported compression methods to prevent malware analysis. What is the best way to bypass #Malware analysis on #Android ? Checkout the local and central Zipfile header of APK 2f371969faf2dc239206e81d00c579ff and tell us what you see.
Security Affairs
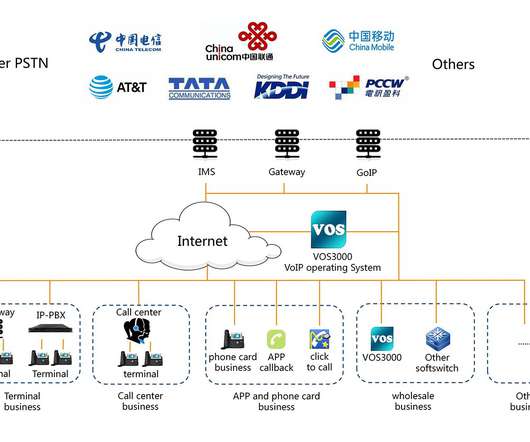
SEPTEMBER 10, 2020
ESET researchers discovered a new piece of malware dubbed CDRThief targets a specific Voice over IP system to steal call data records (CDR). The VoIP platform Linknat VOS2009 and VOS3000 targeted by the malware is used by two China-produced softswitches (software switches). ” reads the analysis published by ESET.
Security Affairs
JULY 9, 2020
Researchers from Malwarebytes have found yet another phone with pre-installed malware via the Lifeline Assistance program sold in the United States. Researchers at Malwarebytes have found malware pre-installed on smartphones sold in the United States, this is the second time as documented in a report published in January.

Malwarebytes
MARCH 22, 2023
Malware authors are artificially pumping up the size of the document in order to try and fool or break security tools. Macros, used to automate aspects of your documents , are a tried and tested way of infecting a PC with malware. Malware authors know this, and will do everything in their power to make you enable them.

Security Affairs
JULY 28, 2020
US and UK cybersecurity agencies issued a joint advisory about the spread of QSnatch Data-Stealing Malware that already infected over 62,000 QNAP NAS devices. The QSnatch malware implements multiple functionalities, such as: . The experts were alerted about the malware in October and immediately launched an investigation.

Security Affairs
MAY 30, 2022
Experts pointed out that the malware is being actively developed. Gafgyt is a popular choice for launching large-scale DDoS attacks, it first appeared in the threat landscape in 2014. The malware can quickly adopt one-day vulnerabilities (within days of a published proof of concept).” LFI CVE-2018-16763 Fuel CMS 1.4.1
Security Affairs
AUGUST 13, 2020
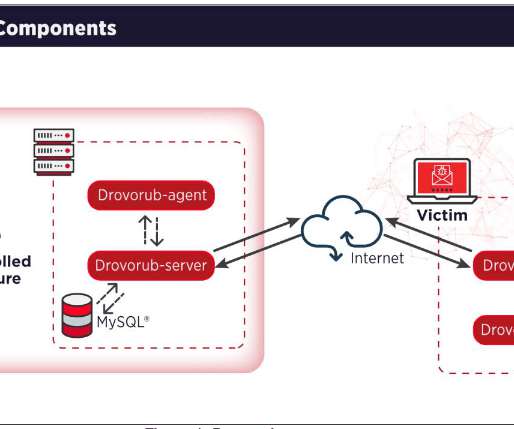
The FBI and NSA issue joint alert related to new Linux malware dubbed Drovorub that has been used by the Russia-linked APT28 group. The FBI and NSA have published a joint security alert containing technical details about a new piece of Linux malware, tracked as Drovorub , allegedly employed by Russia-linked the APT28 group.
Security Affairs
MARCH 5, 2020
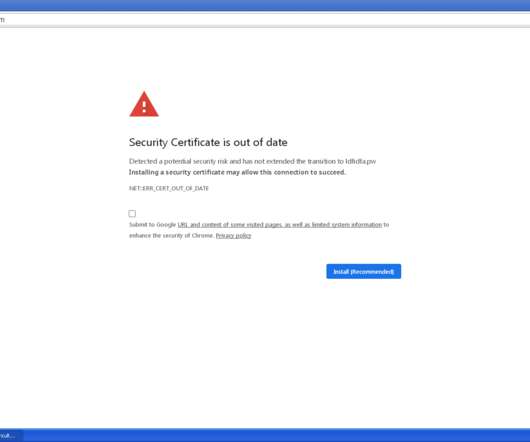
Crooks are using a new phishing technique to trick victims into accepting the installation of a security certificate update and deliver malware. We have already observed threat actors distributing malware masqueraded by legitimate software updates. . Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->.

Security Affairs
FEBRUARY 23, 2020
ISS , the multinational Denmark-based facility services company, was hit with a malware that shuts down shared IT services worldwide. ISS , the Danish multinational services company announced it was hit with malware, in response to the incident the firm disabled access to shared IT services worldwide. Pierluigi Paganini.

Security Affairs
APRIL 16, 2020
The shipping giant Mediterranean Shipping Company (MSC) was victim of a malware-based attack that caused an outage recently. The shipping giant Mediterranean Shipping Company (MSC) discloses a malware-based attack that took place on April 10. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->.

Security Affairs
NOVEMBER 22, 2019
The Payment solutions giant Edenred disclosed a malware incident that affected some of its computing systems, it immediately started an investigation. The Payment solutions giant Edenred announced that some of its computing systems have been infected with malware, the company is currently investigating the incident. Pierluigi Paganini.

Security Affairs
MARCH 13, 2020
. “We recently discovered a new strain of Android malware. “Malware could steal cookie files of any website from other apps in the same way and achieve similar results.” bood, it launches a local server and executes the command that the passed by the Cookiethief malware. SecurityAffairs – malware, Android).

Security Affairs
MARCH 8, 2020
Experts uncovered a new Coronavirus (COVID-19 ) -themed campaign that is distributing a malware downloader that delivers the FormBook information-stealing Trojan. Experts at MalwareHunterTeam uncovered a new malspam campaign exploiting the fear in the Coronavirus (COVID-19) to deliver malware. states the analysis published by FireEye.
Security Affairs
JULY 13, 2020
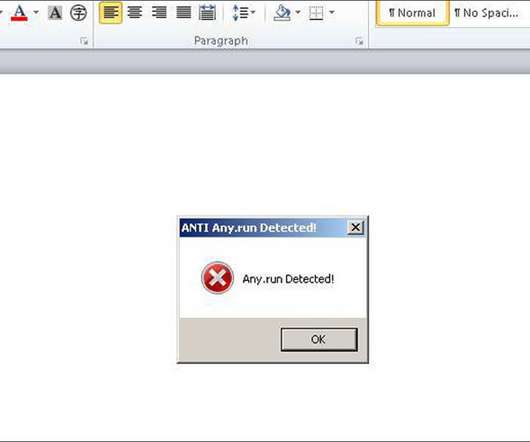
Malware authors are implementing the capability to check if their malicious code is running in the Any.Run malware analysis service. Vxers are implementing the capability to check if their malware is running in the Any.Run interactive online malware sandbox to prevent them from being analyzed by experts. ’ and exit.

Security Affairs
APRIL 29, 2021
Cybersecurity firm Kaspersky discovered a new strain of malware that is believed to be part of the arsenal of theUS Central Intelligence Agency (CIA). Cybersecurity firm Kaspersky has discovered a new malware that experts attribute to the US Central Intelligence Agency. We therefore named this malware Purple Lambert.”

Security Affairs
MARCH 24, 2019
Malware researcher and founder of Yoroi Marco Ramilli shared a simple tool for malware static analysis he used to perform massive Malware analysis research. Malware Static Analysis. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. Malware Static Analysis. Pierluigi Paganini.

SiteLock
AUGUST 27, 2021
According to the report “A resurgence of RAM scraping malware is the most prominent tactical development in 2013,” the same tactic used in the giant Target breach. Out of the 198 Point-of-Sale attacks investigated by Verizon last year, all resulted in sensitive data being exposed.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content