5 Major Cybersecurity Trends to Know for 2024
eSecurity Planet
DECEMBER 19, 2023
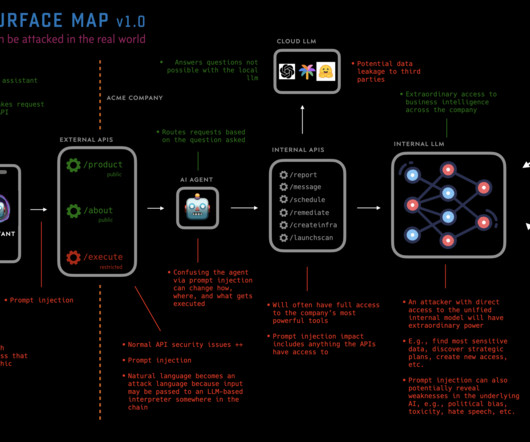
As 2023 draws to an end and cybersecurity budgeting is nearly complete, it helps to consider the year’s events and try to predict next year’s trends. After receiving input from industry experts and doing my own analysis of the year’s driving forces, I identified five major cybersecurity trends. We each need to consider how these trends may affect our organizations and allocate our budgets and resources accordingly: AI will turbo-charge cybersecurity and cyberthreats: Artificial intelligence (AI































Let's personalize your content