Beware: GitHub's Fake Popularity Scam Tricking Developers into Downloading Malware
The Hacker News
APRIL 10, 2024
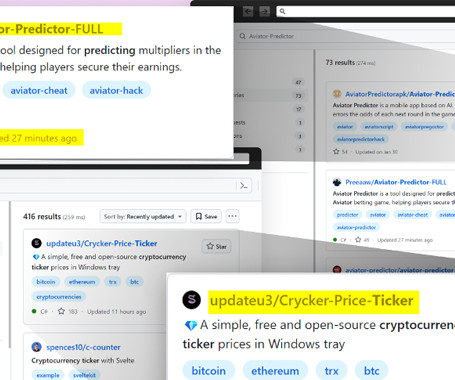
Threat actors are now taking advantage of GitHub's search functionality to trick unsuspecting users looking for popular repositories into downloading spurious counterparts that serve malware.












































Let's personalize your content