What Is Identity and Access Management (IAM)?
Tech Republic Security
FEBRUARY 23, 2024
Learn more about IAM and its importance in securing digital identities and managing access privileges in this comprehensive guide.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 access-management
access-management 
Tech Republic Security
FEBRUARY 23, 2024
Learn more about IAM and its importance in securing digital identities and managing access privileges in this comprehensive guide.

Security Affairs
FEBRUARY 18, 2024
SolarWinds addressed three critical vulnerabilities in its Access Rights Manager (ARM) solution, including two RCE bugs. SolarWinds has fixed several Remote Code Execution (RCE) vulnerabilities in its Access Rights Manager (ARM) solution. Critical 02/06/2024 02/06/2024 SolarWinds Access Rights Manager (ARM) 2023.2.3
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
MAY 31, 2023
The world of Identity and Access Management ( IAM ) is rapidly evolving. Related: Stopping IAM threats IAM began 25 years ago as a method to systematically grant human users access to company IT assets. Today, a “user” most often is a snippet of code seeking access at the cloud edge.

Security Boulevard
APRIL 1, 2024
AI revolutionizes access management by enabling intelligent provisioning, dynamic access control, and fraud prevention. Using machine learning and predictive analytics, it ensures consistent access policies and detects anomalous behavior in real time.

Speaker: Ronald Eddings, Cybersecurity Expert and Podcaster
By focusing on SaaS security posture management, your team can finally accomplish the following: Discover both known and unknown SaaS apps. Deliver better insights on user access and app utilization that’s needed for better IT management and cost optimization across all SaaS apps.

Heimadal Security
FEBRUARY 1, 2024
Looking to find the right privileged access management (PAM) solution for your organization? But knowing where to […] The post Top 11 Privileged Access Management Solutions (2024) appeared first on Heimdal Security Blog.

Heimadal Security
FEBRUARY 9, 2024
Demand for Identity and Access Management tools is booming. Today, there are dozens of Identity and Access Management tools on the market. This can make choosing between providers very […] The post The 11 Best Identity and Access Management Tools (2024) appeared first on Heimdal Security Blog.

Security Affairs
OCTOBER 23, 2023
Researchers discovered three critical remote code execution vulnerabilities in the SolarWinds Access Rights Manager (ARM) product. Security researchers discovered three critical remote code execution vulnerabilities in the SolarWinds Access Rights Manager (ARM) product. The three critical RCE flaws are: CVE-2023-35182 (9.8

Tech Republic Security
FEBRUARY 1, 2023
Without appropriate access management controls, businesses are at significant risk from the loss or theft of both physical and digital assets. Access management controls establish who is allowed the appropriate level of access in order to do their jobs, while reducing the potential for damage or harm to the company.
Heimadal Security
FEBRUARY 6, 2024
So have all the cloud security challenges been solved? […] The post A Guide to Effective Cloud Privileged Access Management appeared first on Heimdal Security Blog. The days of enterprises and heavily regulated companies citing security as the main barrier to cloud adoption are over.

Tech Republic Security
APRIL 20, 2022
Identity and access management software helps you maintain control of your environment by allowing authorized users to access company resources. The post Top IAM tools 2022: Compare identity and access management solutions appeared first on TechRepublic.

Heimadal Security
JANUARY 16, 2024
Key takeaways: Why privileged access management requires a continuous approach; The common pitfalls of poor privileged access management; How to create an effective, end-to-end privileged access management lifecycle. But getting it right isn’t always straightforward.

Bleeping Computer
SEPTEMBER 28, 2023
Cisco is warning of five new Catalyst SD-WAN Manager products vulnerabilities with the most critical allowing unauthenticated remote access to the server. [.]

Security Boulevard
OCTOBER 18, 2023
The post 8 Key Strategies For Hardening Your Identity and Access Management Security appeared first on AppOmni. The post 8 Key Strategies For Hardening Your Identity and Access Management Security appeared first on Security Boulevard.

Security Boulevard
DECEMBER 9, 2022
Learn how to secure your vital organizational or personal data by understanding the role of identity access and management for SaaS applications. The post SaaS Identity Access Management for Shadow IT appeared first on Security Boulevard.

The Last Watchdog
NOVEMBER 8, 2021
This data is managed by different entities, such as primary care facilities, acute care facilities and within associated applications that collect, store and track health data, creating numerous exposure vulnerabilities. The vast majority of breaches are the result of poorly managed access controls. Security-privacy teamwork.

CSO Magazine
MAY 26, 2022
One of the main objectives of the bad guys is to escalate to privileged account access wherever possible. As a result, organizations recognize that they need to take special care with the way that they manage and grant access to the most powerful privileged accounts in their environments.

Heimadal Security
MAY 5, 2023
Identity and Access Management is a critical component of modern-day cybersecurity. Now […] The post Identity and Access Management Best Practices appeared first on Heimdal Security Blog.

The Last Watchdog
JUNE 21, 2023
To be productive in an interconnected work environment, employees need immediate access to numerous platforms, both on- and off-premises. Some nine out of ten cyberattacks are estimated to begin with a threat actor gaining unauthorized access to a computer system via poorly managed access credentials.

Heimadal Security
NOVEMBER 23, 2023
Privileged Access Management is a cybersecurity instrument that any safety-oriented company should have. Key takeaways of this Privileged Access […] The post Privileged Access Management – An Insider’s Fast-Forward Guide appeared first on Heimdal Security Blog.

Security Boulevard
FEBRUARY 25, 2024
For example, a tech team might find that Jira works well for managing tasks and a support team might find they prefer PagerDuty to handle support tickets. This is where webhooks step in as a middleware […] The post Using Webhooks with your Privileged Access Management Tool appeared first on Security Boulevard.

Security Boulevard
JANUARY 10, 2024
Privileged Access Management (PAM) plays a crucial role in the security of any organization. Within PAM, the aspect of just-in-time self-service access has become increasingly important.

Heimadal Security
NOVEMBER 10, 2022
Privileged access management, PAM in short, is a crucial set of tools and technologies allowing organizations to maintain steadfast control and monitorization over the access to critical information and resources, as well as users, accounts and processes.

Security Boulevard
MARCH 18, 2022
The post Zero-Trust’s Foundation is Identity and Access Management appeared first on Security Boulevard. The cause: A ransomware attack on fuel distribution company Colonial Pipeline, made possible by the most common kind of attack—misused or stolen credentials.

Heimadal Security
NOVEMBER 17, 2023
But how exactly can you identify how privileged access is handled within […] The post How to Conduct a Successful Privileged Access Management Audit appeared first on Heimdal Security Blog. This threat demands more than just awareness; it requires a strategic and thorough response.

Tech Republic Security
NOVEMBER 14, 2022
The post Data encryption as a crucial step to manage data access and security appeared first on TechRepublic. With data breaches on the rise, encryption has never been more important for protecting companies against hackers and cyberattacks.

The Hacker News
MARCH 11, 2024
As cyber threats loom around every corner and privileged accounts become prime targets, the significance of implementing a robust Privileged Access Management (PAM) solution can't be overstated.

Tech Republic Security
MAY 4, 2022
Auth0 and JumpCloud are two popular identity and access management software solutions. The post Auth0 vs JumpCloud: Compare identity and access management software appeared first on TechRepublic. How do these IAM solutions compare, and which one is right for your business?

Thales Cloud Protection & Licensing
MAY 23, 2022
Access Management is Essential for Strengthening OT Security. These systems are connected to and managed from the cloud to fine-tune performance, provide data analytics, and ensure the integrity of critical infrastructure across all sectors. Access management is an essential mitigation strategy.
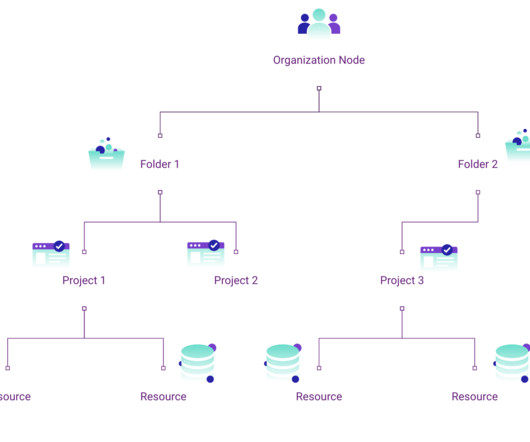
Security Boulevard
DECEMBER 18, 2023
If you’re an enterprise operating out of Google Cloud, you’re likely looking for ways to manage access, enforce guardrails, and make configuration constraints to resources across your organization.
Cisco Security
JULY 23, 2021
You can empower them to focus on your strategic priorities by adopting Cisco Secure Managed Remote Access. Secure Managed Remote Access is our scalable cloud service that frees your IT and security teams to get back their focus on critical tasks, offloading routine remote access management to a trusted partner.
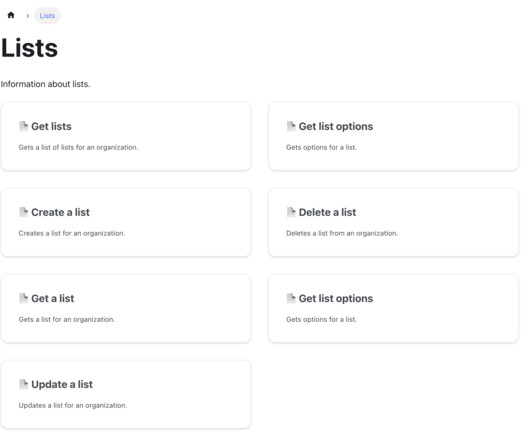
Security Boulevard
MARCH 14, 2024
Impart Security is proud to introduce Runtime Lists API, a groundbreaking feature designed to streamline how security teams manage Access Control Lists (ACLs). This innovation greatly simplifies the complex, time-consuming task of managing ACLs across multiple platforms and large, widely dispersed teams of security analysts.
Security Boulevard
MAY 9, 2023
Unified Privileged Access Management (UPAM)SafePaaS announces Unified Privileged Access Management (UPAM) for Operating Systems, Databases, Applications, and Cloud Infrastructure at Digital Trust World.Boston, Massachusetts, May 9, 2023.

The Last Watchdog
SEPTEMBER 26, 2022
In fact, the 2022 Verizon Data Breach Investigation Report revealed an alarming 13 percent increase in ransomware attacks overall – greater than past five years combined – and the inability to properly manage identities and privileges across the enterprise is often the root cause. the crown jewels are on endpoints or accessed from these.

Heimadal Security
NOVEMBER 16, 2021
To understand what privileged access management is, we need to first understand what privileged access refers to. What Is Privileged Access? A simple definition for privileged access would be that speaking […]. A simple definition for privileged access would be that speaking […].

Heimadal Security
MAY 23, 2023
Thus, in the attempt of preventing unauthorized third parties from accessing their accounts and sensitive data, companies are increasingly turning to biometric authentication.

Security Boulevard
APRIL 4, 2023
Identity and Access Management (IAM) is a critical component of cybersecurity, especially in business environments. IAM, in simple terms, is a framework of policies, practices and procedures to ensure that the right users have access to the right resources and systems at the right time.

Tech Republic Security
APRIL 26, 2022
The post JumpCloud vs Okta: Compare identity and access management software appeared first on TechRepublic. Read this feature comparison of JumpCloud and Okta, two leading IAM softwares solutions that can help secure your business.

Security Boulevard
APRIL 5, 2022
Teleport today made available an update to its access management platform that can now also apply an identity to software. In addition, Teleport 9 makes a Teleport Desktop Access module generally available with support for Windows session recordings, copy-and-paste via a clipboard and multifactor authentication included.

Security Boulevard
JUNE 9, 2023
Learn how to effectively manage risks associated with identity and access management with the comprehensive guide. The post How to Manage Risks Associated with Identity and Access Management? Start protecting your business today. appeared first on Security Boulevard.

Security Boulevard
MARCH 14, 2024
The post Is Your Approach to Workload Identity and Access Management Mature Enough? The post Is Your Approach to Workload Identity and Access Management Mature Enough? 2 min read Take this self-assessment to guide you toward uncovering potential weaknesses with your strategy for securing workload connections.

Heimadal Security
NOVEMBER 25, 2022
One of the first steps to successfully implementing a privileged access management (PAM) solution is defining clear and consistent policies that everyone who uses and manages privileged accounts understands and accepts. […]. The post What Is a Privileged Access Management (PAM) Policy?

Heimadal Security
APRIL 8, 2022
Identity and access management is a key component in ensuring the security of data. It can be used to protect companies against data breaches by providing a layer of security that protects information from unauthorized access.

Security Boulevard
SEPTEMBER 15, 2021
In any organization, big or small, employees are given access to critical information, files, data, and more. The post How User Access Reviews Manage Insider Threats appeared first on SecureLink. The post How User Access Reviews Manage Insider Threats appeared first on SecureLink.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content