How to Stop Shadow IT, Manage Access and Ensure Security with Cloud Applications
Webroot
FEBRUARY 2, 2021
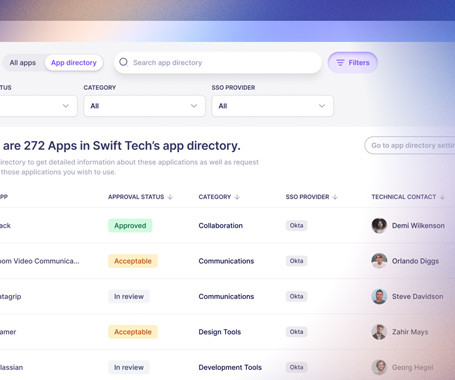
Today, the average enterprise uses over 2000 cloud applications and services , and we expect this number will continue to grow as more businesses realize the efficiency, flexibility and collaboration benefits these services bring. When implementing these types of solutions, security should be a central concern in the vetting process.

















































Let's personalize your content