VulnRecap 3/11/24 – JetBrains & Atlassian Issues Persist
eSecurity Planet
MARCH 11, 2024
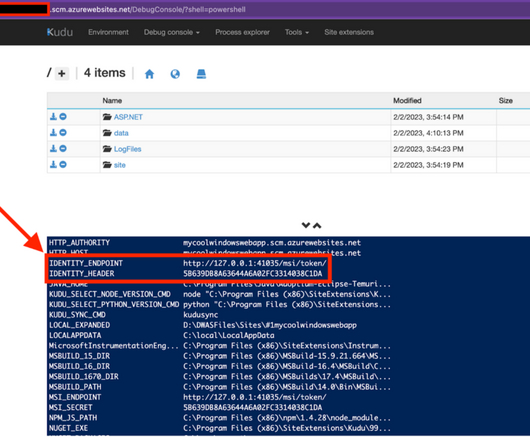
And all IT and security teams should follow vulnerability news for vendor bulletins and updates. March 4, 2024 JetBrains Server Issues Continue with New Vulnerabilities Type of vulnerability: Authentication bypass. The problem: On March 5, Apple released a security notice for its new operating systems, iOS 17.4 and iPadOS 17.4.













































Let's personalize your content