Credential Flusher, understanding the threat and how to protect your login data
Security Affairs
SEPTEMBER 18, 2024
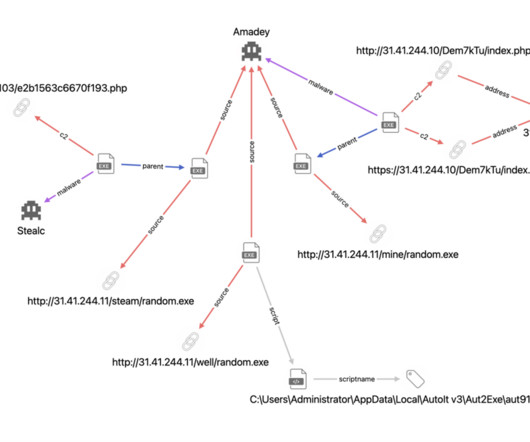
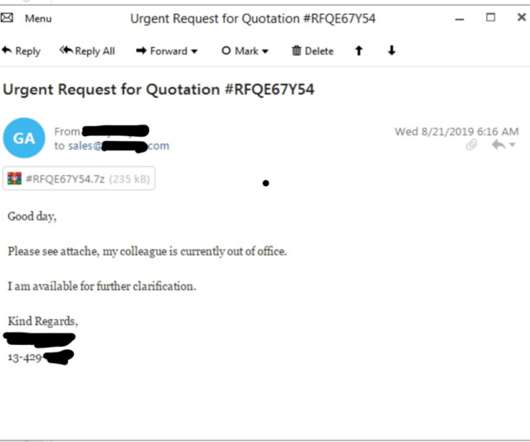
Script code snippet – Credit OALABS The attackers hope that the victim will save the password when asked by the browser, so that it will be stolen by StealC running. Enable 2FA Authentication: This measure adds an extra layer of security by requiring a second factor of authentication in addition to the password.















































Let's personalize your content