Credential Flusher, understanding the threat and how to protect your login data
Security Affairs
SEPTEMBER 18, 2024
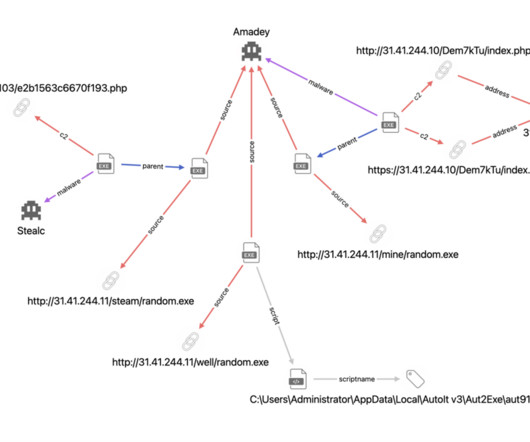
The malware is distributed via the Amadey loader ( [link] ), which can be spread through phishing e-mails or downloads from compromised sites. Why and how to protect ourselves Once the credentials are stolen, hackers can use them to access various online accounts, including banking, e-mail, and social media accounts.


























Let's personalize your content