How to Become Great at API Key Rotation: Best Practices and Tips
Security Boulevard
DECEMBER 28, 2023
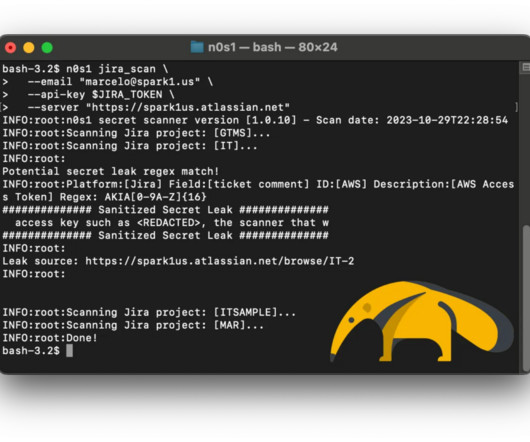
Secret management can be a complex challenge, especially when you are trying to do it in a way that is right for security. Key rotation is a big piece of that puzzle. In this article, we will take you from zero to hero on key rotation.
















































Let's personalize your content