Heimdal™ Security Rolls Out Patch & Asset Management for Linux Systems
Heimadal Security
FEBRUARY 24, 2022
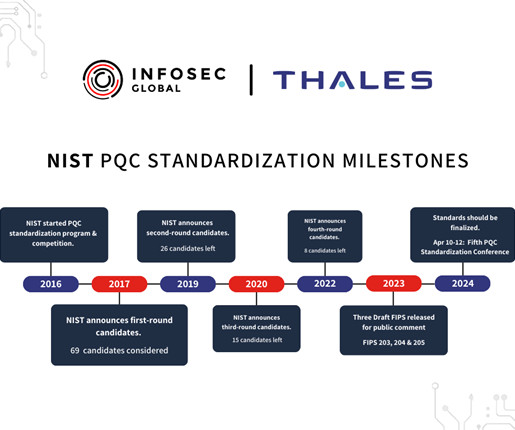
Heimdal™ has recently unveiled its newest addition to the Patch & Asset Management suite – the patch and vulnerability management module for Linux systems. With the latest inclusion, Heimdal takes one step further towards bridging the compatibility gap in automatic patch management.














































Let's personalize your content