Are DDoS Simulation Tests Legal?
Security Boulevard
JANUARY 14, 2024
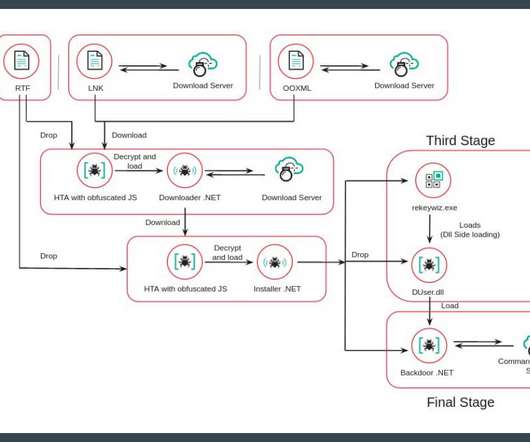
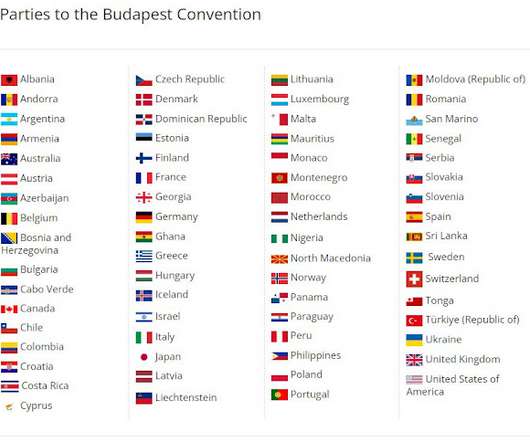
DDoS simulation tests fall into a different legal category than real DDoS attacks carried out by hackers. However, the law also specifies that the action must be “without authorization […] The post Are DDoS Simulation Tests Legal? appeared first on Security Boulevard.















































Let's personalize your content