Android pre-installed apps are affected by high-severity vulnerabilities
Security Affairs
MAY 27, 2022
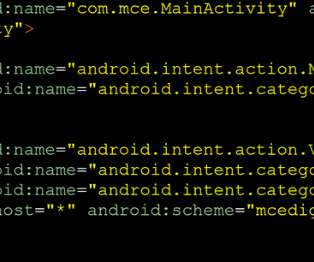
The experts pointed out that the vulnerabilities affected apps with millions of downloads, the good news is that the flaws have been fixed. The bad news is that some of the affected apps cannot be fully uninstalled or disabled without root access to the device. ” reads the post published by Microsoft. To nominate, please visit:?.















































Let's personalize your content