A Scammer Tried to Scare Me into Buying Their Security Services - Here's How It Went Down
Troy Hunt
MARCH 26, 2018
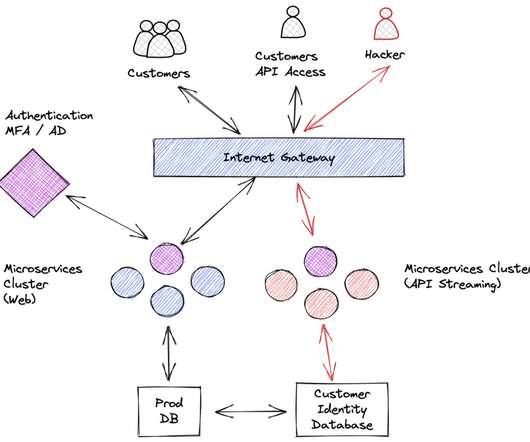
Shofiur R" found troyhunt.com on a "free online malware scanner" and tried to scare me into believing my site had security vulnerabilities then shake me down for a penetration test. I don’t know whether I should thank him for his candour or rip into him for attempting to profit without verifying the “vulnerabilities”.






















Let's personalize your content