German arms manufacturer Rheinmetall suffered Black Basta ransomware attack
Security Affairs
MAY 23, 2023
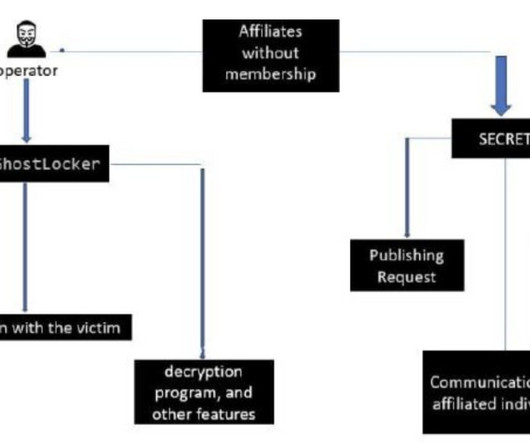
The German automotive and arms manufacturer Rheinmetall announced it was victim of a Black Basta ransomware attack that took place last month. The company this week announced it was victim of a ransomware attack conducted by the Black Basta ransomware group.










































Let's personalize your content