More ways for users to identify independently security tested apps on Google Play
Google Security
NOVEMBER 2, 2023
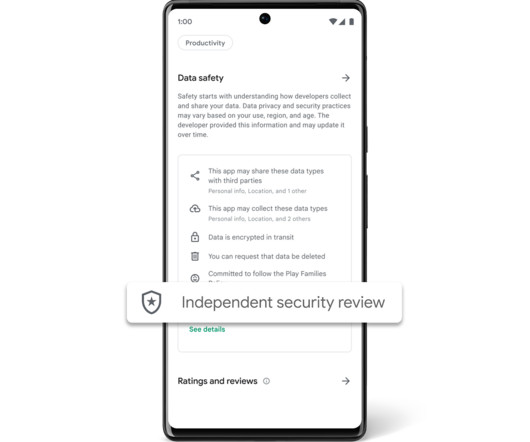
Posted by Nataliya Stanetsky, Android Security and Privacy Team Keeping Google Play safe for users and developers remains a top priority for Google. Research shows that transparent security labeling plays a crucial role in consumer risk perception, building trust, and influencing product purchasing decisions.
















































Let's personalize your content