In What ways do CVSS v3 and CVSS v4 differ?
Security Boulevard
NOVEMBER 20, 2023
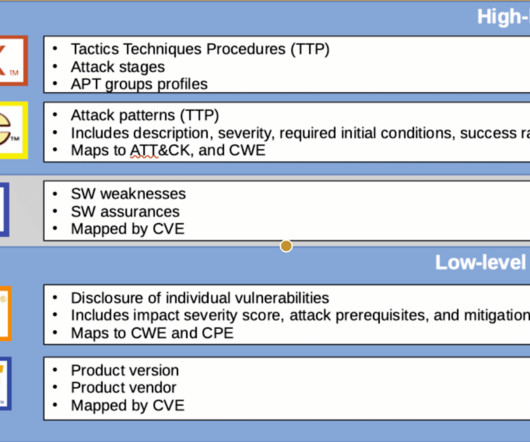
Specialists utilize the Common Vulnerability Scoring System (CVSS) as a critical foundation for assessing and ranking cybersecurity vulnerabilities. When it comes to the methodology used to determine the severity of vulnerabilities, version 4 is a significant advancement over version 3.

































Let's personalize your content