Social Engineering from the Attacker Perspective
Security Through Education
FEBRUARY 9, 2022
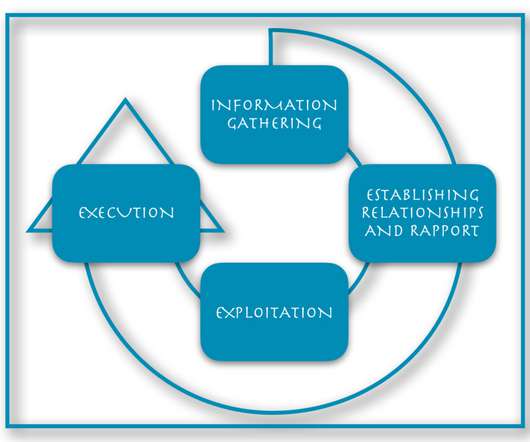
Rather, it encompasses how we communicate with our parents, therapists, children, spouses, and others. Rather, it encompasses how we communicate with our parents, therapists, children, spouses, and others. No matter how you define social engineering, it can be used for good or bad, just like anything else. Breaking it Down.































Let's personalize your content