Russian spies are attempting to tap transatlantic undersea cables
Security Affairs
MARCH 1, 2020
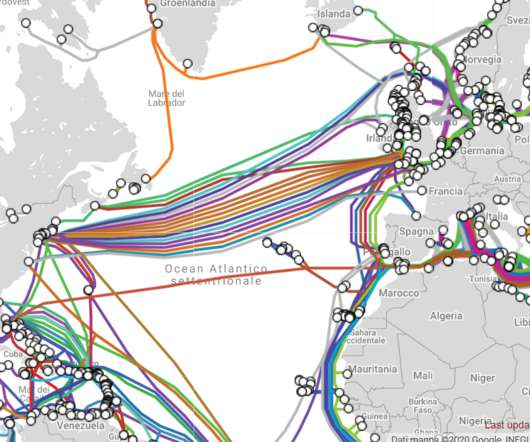
This week, several media reported that agents of the Russian intelligence reportedly went to Ireland to inspect the undersea cables. Ireland is a strategic place for intercontinental communications because it represents the place where undersea cables which carry internet traffic connect to Europe. ” reported The Sunday Times.

















Let's personalize your content