A Deep Dive into DDoS Carpet-Bombing Attacks
Security Boulevard
OCTOBER 15, 2024
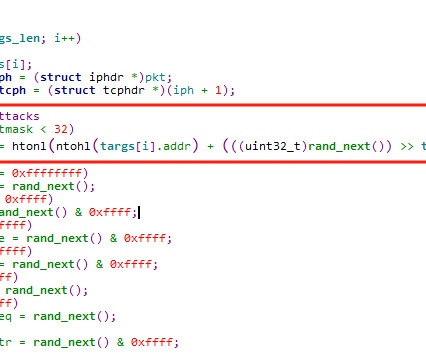
With the rapid growth of the internet, especially in areas like cloud computing, 5G, and IoT technologies, the scale of botnets continues to expand, intensifying the battle between attack and defense. In response, DDoS attacks have evolved, taking on a more intelligent form to evade security defenses.














Let's personalize your content