Registry Explorer is the registry editor every Windows user needs
Bleeping Computer
AUGUST 1, 2021
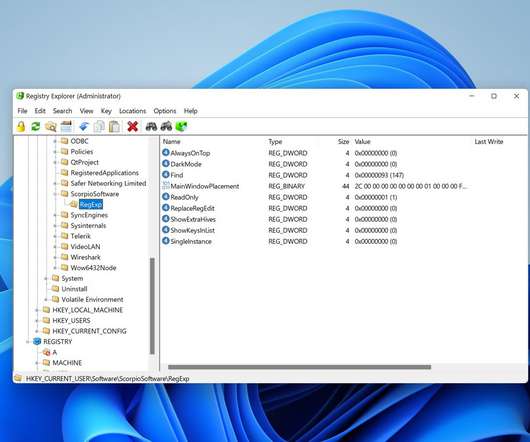
Last week, a new open-source Registry Editor was released that puts Windows Regedit software to shame by supporting a host of advanced features, making editing the Registry easier than ever. [.].



























Let's personalize your content