Mozilla Drops Onerep After CEO Admits to Running People-Search Networks
Krebs on Security
MARCH 22, 2024
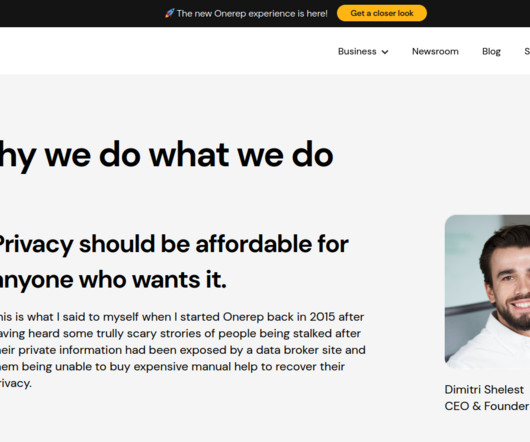
The nonprofit organization that supports the Firefox web browser said today it is winding down its new partnership with Onerep , an identity protection service recently bundled with Firefox that offers to remove users from hundreds of people-search sites. The move comes just days after a report by KrebsOnSecurity forced Onerep’s CEO to admit that he has founded dozens of people-search networks over the years.








































Let's personalize your content