Decoupling for Security
Schneier on Security
NOVEMBER 8, 2023
This is an excerpt from a longer paper. You can read the whole thing (complete with sidebars and illustrations) here. Our message is simple: it is possible to get the best of both worlds. We can and should get the benefits of the cloud while taking security back into our own hands. Here we outline a strategy for doing that. What Is Decoupling? In the last few years, a slew of ideas old and new have converged to reveal a path out of this morass, but they haven’t been widely recognized, comb

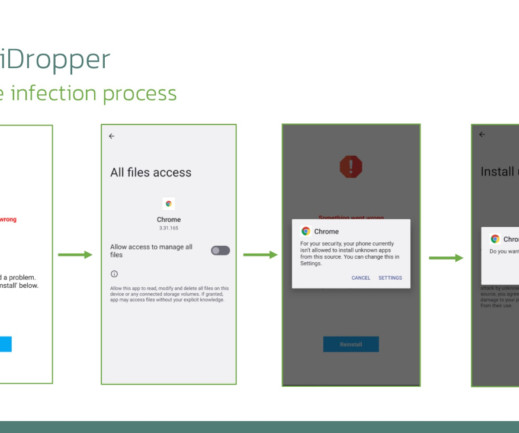






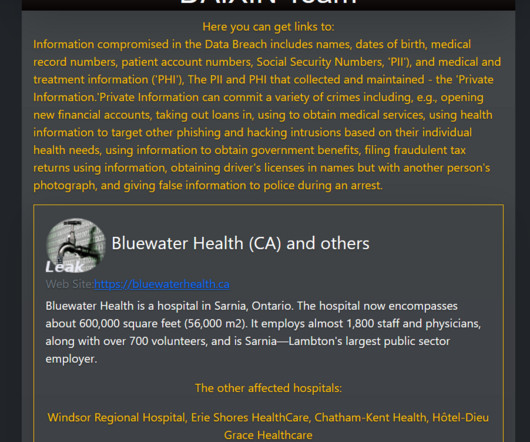

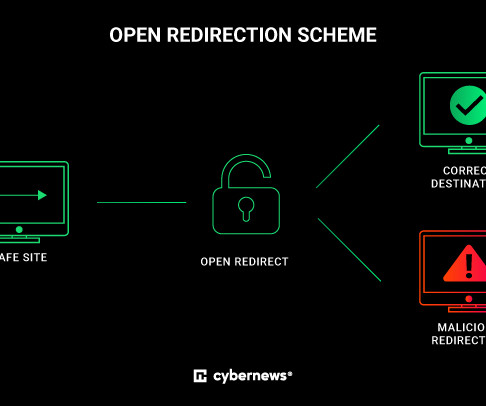





























Let's personalize your content