A little Machine Learning “Magic”…
NopSec
APRIL 29, 2015
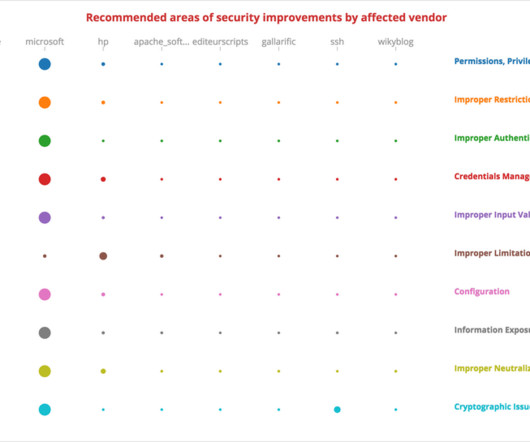
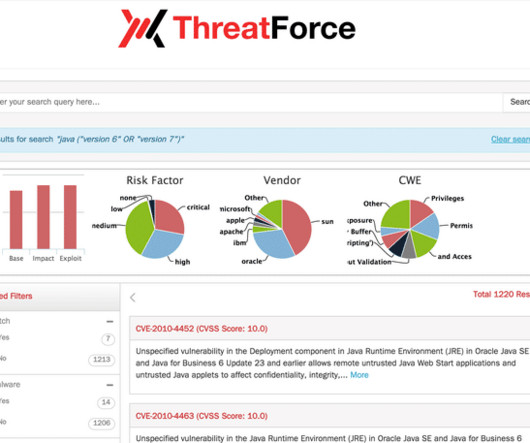
This blog post is the first of a series documenting the journey into Machine Learning Algorithms NopSec is undertaking as part of Unified VRM data analytics capabilities. In our last sprint, as part of Unified VRM, we started using Machine Learning – [link] – to spot trends in past clients vulnerability data in order to abstract areas of the security program that need improvement in the future.













Let's personalize your content