ChatGPT: Hopes, Dreams, Cheating and Cybersecurity
Lohrman on Security
JANUARY 29, 2023
ChatGPT is an AI-powered chatbot created by OpenAI. So what are the opportunities and risks with using this technology across different domains?

Lohrman on Security
JANUARY 29, 2023
ChatGPT is an AI-powered chatbot created by OpenAI. So what are the opportunities and risks with using this technology across different domains?

Schneier on Security
FEBRUARY 2, 2023
Hacker “Capture the Flag” has been a mainstay at hacker gatherings since the mid-1990s. It’s like the outdoor game, but played on computer networks. Teams of hackers defend their own computers while attacking other teams’. It’s a controlled setting for what computer hackers do in real life: finding and fixing vulnerabilities in their own systems and exploiting them in others’ It’s the software vulnerability lifecycle.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
FEBRUARY 1, 2023
Change Your Password Day — an annual reminder of just how bad passwords really are. The post The headache of changing passwords appeared first on TechRepublic.

Bleeping Computer
FEBRUARY 3, 2023
Admins, hosting providers, and the French Computer Emergency Response Team (CERT-FR) warn that attackers actively target VMware ESXi servers unpatched against a two-year-old remote code execution vulnerability to deploy ransomware. [.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Security Boulevard
JANUARY 31, 2023
API sprawl, which Brian Otten, VP of the digital transformation catalysts division with Axway, defined as “an uncontrolled proliferation of APIs in an organization,” is creating a flood of new security headaches for organizations. One of the biggest problems in providing security for APIs is that sprawl makes them difficult to track and inventory. And.

Schneier on Security
JANUARY 31, 2023
Chainalysis reports that worldwide ransomware payments were down in 2022. Ransomware attackers extorted at least $456.8 million from victims in 2022, down from $765.6 million the year before. As always, we have to caveat these findings by noting that the true totals are much higher, as there are cryptocurrency addresses controlled by ransomware attackers that have yet to be identified on the blockchain and incorporated into our data.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
FEBRUARY 1, 2023
Google Fi, Google's U.S.-only telecommunications and mobile internet service, has informed customers that personal data was exposed by a data breach at one of its primary network providers, with some customers warned that it allowed SIM swapping attacks. [.

Security Boulevard
JANUARY 30, 2023
Security and compliance risks are ranked as among the top barriers to achieving value from investments moving to the cloud as organizations grapple with what they consider an “urgent priority,” according to a recent report from Accenture. The global survey of 800 business and IT leaders revealed security continues to be one of the top. The post Security, Compliance Risks Complicate Cloud Migration Efforts appeared first on Security Boulevard.

Schneier on Security
FEBRUARY 1, 2023
This is the result of a security audit: More than a fifth of the passwords protecting network accounts at the US Department of the Interior—including Password1234, Password1234!, and ChangeItN0w!—were weak enough to be cracked using standard methods, a recently published security audit of the agency found. […] The results weren’t encouraging.
Tech Republic Security
FEBRUARY 1, 2023
A new business email attack threat actor is using a stealth tactic to avoid giveaways of typical social engineering attacks. Learn the best defense for protecting your company. The post New cybersecurity BEC attack mimics vendors appeared first on TechRepublic.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Bleeping Computer
FEBRUARY 2, 2023
An ongoing Google ads malvertising campaign is spreading malware installers that leverage KoiVM virtualization technology to evade detection when installing the Formbook data stealer. [.

CSO Magazine
JANUARY 30, 2023
The security poverty line broadly defines a divide between the organizations that have the means and resources to achieve and maintain mature security postures to protect data, and those that do not. It was first coined by cybersecurity expert Wendy Nather in 2011, and the concept is just as relevant today as it was then (if not more so). It has widely become the benchmark for acceptable cybersecurity, often associated with factors such as company size, sector and disposable income, but also kno

Schneier on Security
FEBRUARY 3, 2023
Interesting research: “ Facial Misrecognition Systems: Simple Weight Manipulations Force DNNs to Err Only on Specific Persons “: Abstract: In this paper we describe how to plant novel types of backdoors in any facial recognition model based on the popular architecture of deep Siamese neural networks, by mathematically changing a small fraction of its weights (i.e., without using any additional training or optimization).

Tech Republic Security
FEBRUARY 1, 2023
A new phishing campaign abuses OneNote documents to infect computers with the infamous AsyncRAT malware, targeting users in the U.K., Canada and the U.S. The post OneNote documents spread malware in several countries appeared first on TechRepublic.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Security Boulevard
JANUARY 30, 2023
There is no debate that the software supply chain is filled with action. It’s the front lines of the security world these days. If you have a shadow of a doubt, search the history of SolarWinds, Codecov , or CircleCI for examples of how attackers use the supply chain as a gateway of compromise. The post 6 misconceptions about Software Bills of Materials appeared first on Security Boulevard.
Cisco Security
FEBRUARY 2, 2023
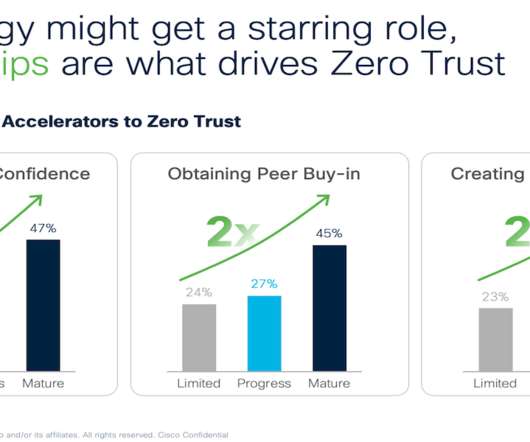
Be impeccable with your words. It’s the first of the Four Agreements – a set of universal life principles outlined in the bestselling book by Don Miguel Ruiz. ‘Being impeccable with your words’ is my favorite, and it’s no surprise. As a product marketer, I spend most of my daily existence casting about for the perfect word to use in web copy, a webinar, or video script.

Dark Reading
FEBRUARY 1, 2023
Killnet is building its profile, inspiring jewelry sales and rap anthems. But the impact of its DDoS attacks, like the ones that targeted 14 major US hospitals this week, remain largely questionable.

Tech Republic Security
FEBRUARY 2, 2023
A new version of the Prilex POS malware has found a novel way to steal your credit card information. The post Prilex POS malware evolves to block contactless transactions appeared first on TechRepublic.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Security Boulevard
JANUARY 30, 2023
One of the most imminent and pressing threats to organizations presently is harvest now, decrypt later (HNDL) attacks. According to a recent poll, half of responding professionals at organizations considering quantum computing benefits believe that their organizations are at risk for HNDL attacks. During an HNDL attack, threat actors will “harvest” encrypted data from unsuspecting.

Bleeping Computer
JANUARY 30, 2023
A U.S. No Fly list with over 1.5 million records of banned flyers and upwards of 250,000 'selectees' has been shared publicly on a hacking forum. BleepingComputer has confirmed, the list is the same TSA No Fly list that was discovered recently on an unsecured CommuteAir server. [.

CSO Magazine
FEBRUARY 2, 2023
State-sponsored threat groups increasingly use ransomware-like attacks as cover to hide more insidious activities. Russian advanced persistent threat (APT) group Sandworm used ransomware programs to destroy data multiple times over the past six months while North Korea's Lazarus group used infrastructure previously associated with a ransomware group for intelligence gathering campaigns.

Tech Republic Security
FEBRUARY 2, 2023
A new study by Salesforce’s MuleSoft suggests more isn’t necessarily better if an organization’s applications are not playing well together. Unfortunately, more than 70% remain disconnected from one another and the core business. The post Study: Companies have upwards of 1,000 apps but only a third are integrated appeared first on TechRepublic.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.
Security Boulevard
JANUARY 31, 2023
Two researchers report vulnerability in KeePass. But lead developer Dominik Reichl says it’s not a problem—and refuses to fix the flaw. The post Another Password Manager Leak Bug: But KeePass Denies CVE appeared first on Security Boulevard.

Bleeping Computer
JANUARY 28, 2023
Security researchers have identified a new data-wiping malware they named SwiftSlicer that aims to overwrite crucial files used by the Windows operating system. [.

CSO Magazine
FEBRUARY 2, 2023
VMware published patches last week for four vulnerabilities in its vRealize Log Insight product that, if combined, could allow attackers to take over the log collection and analytics platform. This week, a proof-of-concept exploit chain has been released by security researchers, along with detailed explanations for each vulnerability, meaning in-the-wild attacks could soon follow.

Tech Republic Security
JANUARY 31, 2023
IT pros typically have access to company servers, network devices and data so they can perform their jobs. However, that access entails risk, including exposure of confidential information and interruption in essential business services. This policy from TechRepublic Premium offers guidelines for governing access to critical systems and confidential data.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.

Security Boulevard
JANUARY 30, 2023
New and Noteworthy: ChatGPT Makes Waves Inside and Outside of the Tech Industry Since it was made publicly available in December, ChatGPT has prompted all sorts of reactions from both inside and outside technology circles. Microsoft, which previously invested $1B into ChatGPT creator company OpenAI, indicated it will invest another $10 billion into the company and that it would incorporate AI into all of Microsoft’s tools. ( 1 ) Cybercriminals also seem to see the potential in ChatGPT; some sec

Bleeping Computer
FEBRUARY 2, 2023
Security researchers warn that hackers may start using Microsoft Visual Studio Tools for Office (VSTO) more often as method to achieve persistence and execute code on a target machine via malicious Office add-ins. [.

Dark Reading
JANUARY 31, 2023
Everyone on Twitter wants a blue check mark. But Microsoft Azure's blue badges are even more valuable to a threat actor stealing your data via malicious OAuth apps.

Tech Republic Security
JANUARY 30, 2023
Learn some of today's most popular attacks and how to mitigate them with The All-in-One Ethical Hacking & Penetration Testing Bundle. The post Get nine ethical hacking courses for just $30 appeared first on TechRepublic.

Speaker: William Hord, Vice President of ERM Services
A well-defined change management process is critical to minimizing the impact that change has on your organization. Leveraging the data that your ERM program already contains is an effective way to help create and manage the overall change management process within your organization. Your ERM program generally assesses and maintains detailed information related to strategy, operations, and the remediation plans needed to mitigate the impact on the organization.
Let's personalize your content