xz Utils Backdoor
Schneier on Security
APRIL 2, 2024
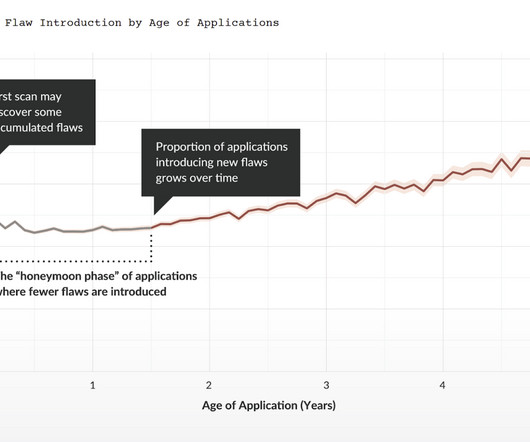
From ArsTehnica : Malicious code added to xz Utils versions 5.6.0 Anyone in possession of a predetermined encryption key could stash any code of their choice in an SSH login certificate, upload it, and execute it on the backdoored device. modified the way the software functions. It was an incredibly complex backdoor.













































Let's personalize your content