How encryption can help address Cloud misconfiguration
Thales Cloud Protection & Licensing
NOVEMBER 15, 2021
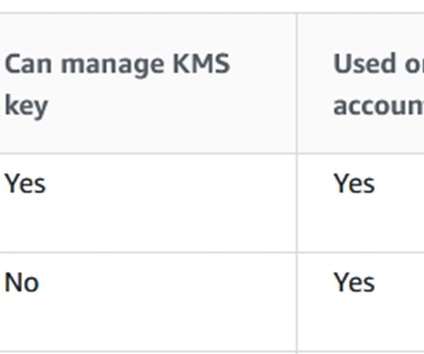
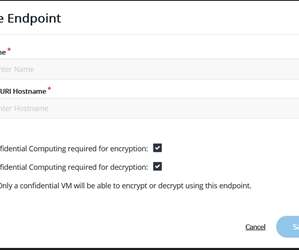
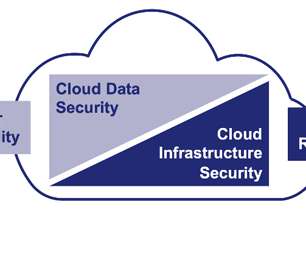
How encryption can help address Cloud misconfiguration. So, whichever way you go, there is, across time, a very high likelihood that a CSP's encryption, tokenization, or key management scheme will be misconfigured either by the CSP itself or by the CSP user. Bring your own encryption (BYOE).
















































Let's personalize your content