Critical Success Factors to Widespread Deployment of IoT
Thales Cloud Protection & Licensing
FEBRUARY 16, 2021
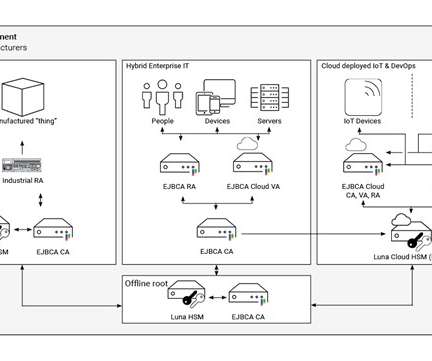
Critical Success Factors to Widespread Deployment of IoT. Digital technology and connected IoT devices have proliferated across industries and into our daily lives. Electric grid utilities are deploying smart meters to better correspond to consumers energy demands while lowering costs. Threat vectors on IoT.

















Let's personalize your content