Best 8 Vulnerability Management Tools for 2024
Centraleyes
MARCH 25, 2024
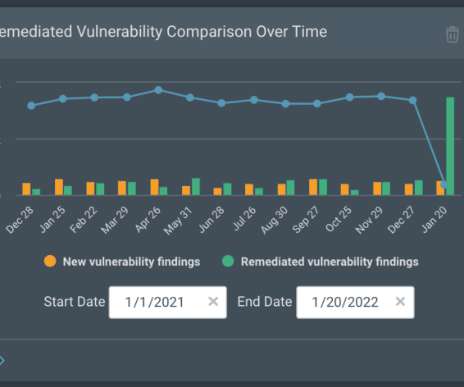
How’s your vulnerability management going? Or perhaps you’re doubting yourself, unsure whether your organization is protected against vulnerability-based attacks. Let’s explore how you can enhance your vulnerability management strategy. What is Vulnerability Management?














































Let's personalize your content