Muddling Meerkat, a mysterious DNS Operation involving China’s Great Firewall
Security Affairs
MAY 1, 2024
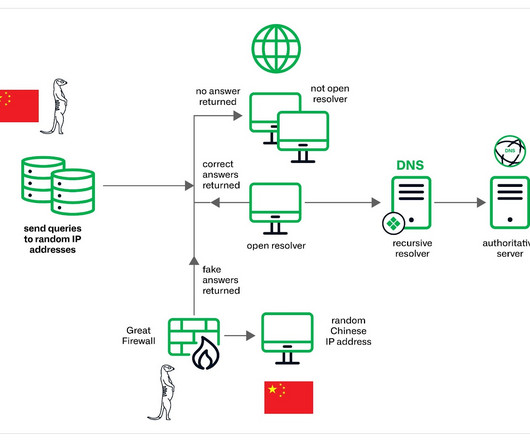
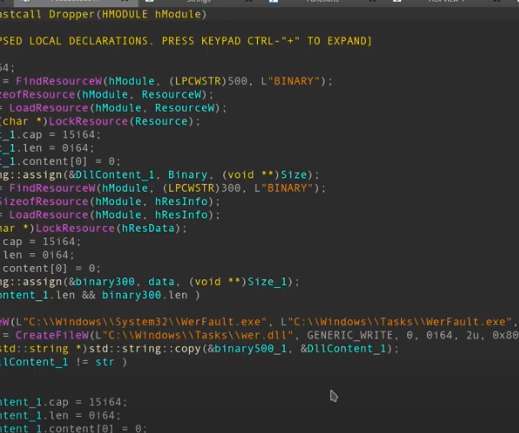
The threat actors appear to have the capability to control China’s Great Firewall and were observed utilizing a novel technique involving fake DNS MX records. The DNS event data containing MX records from the GFW often occurs on separate dates from those where we see MX queries at open resolvers.” ” concludes the report.






































Let's personalize your content