What Are Passkeys?
Duo's Security Blog
JUNE 12, 2023
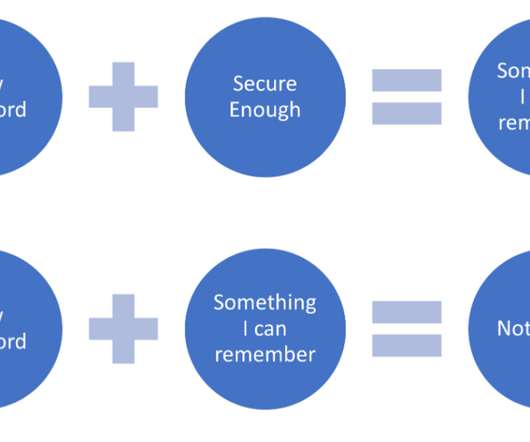
Before we can discuss passkeys, we need to lay some groundwork and discuss authentication, Passwordless and WebAuthn. Authentication is the process of verifying your online identity. This ensures the right people get access to the right online resources. We started with usernames and passwords – something you know.



















Let's personalize your content