Identity Protection Explained in Fewer than 140 Characters
SecureBlitz
OCTOBER 17, 2023
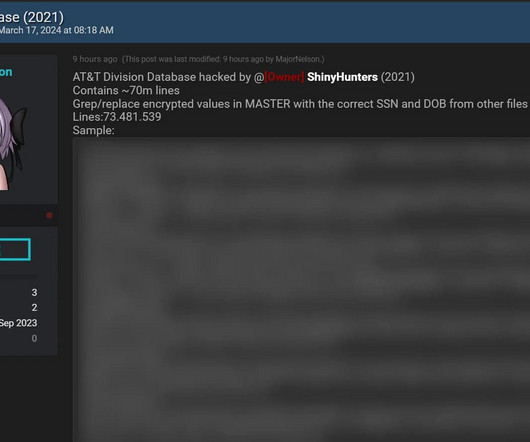
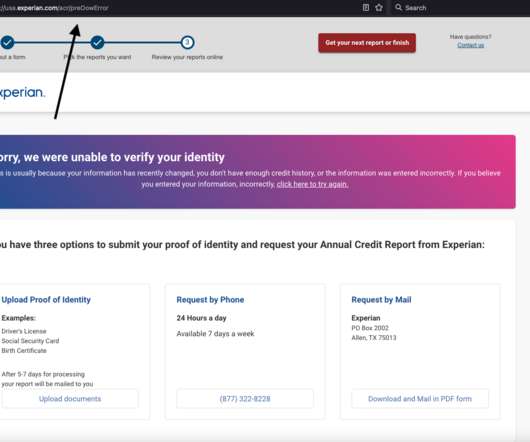
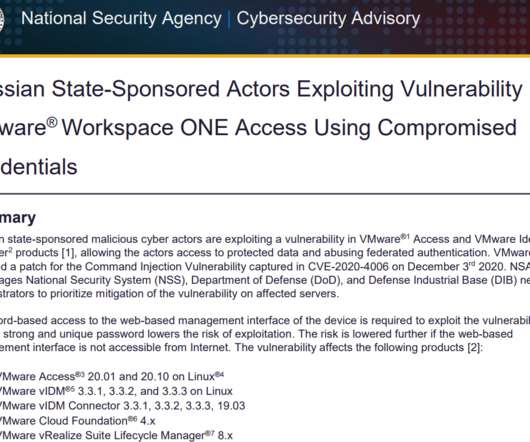
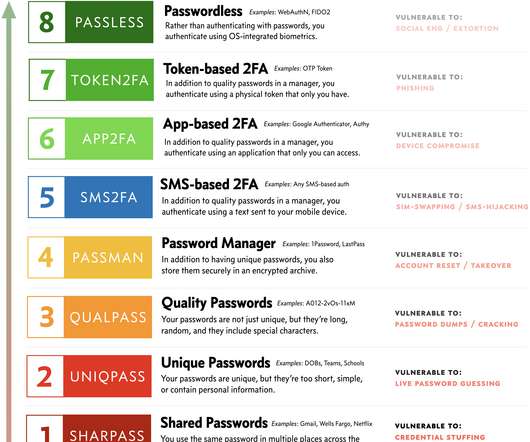
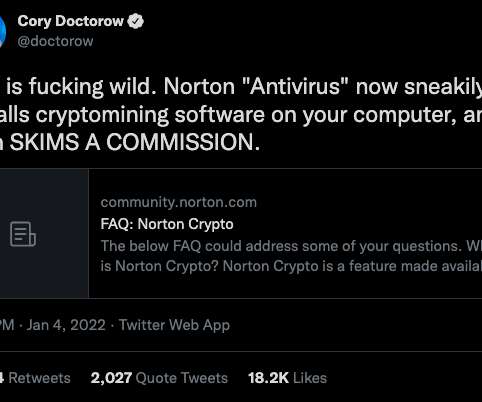
In today's digital age, the protection of our identities has assumed a critical role in our daily lives. The omnipresent threats of identity theft, fraud, and cybercrime underscore the necessity of understanding identity protection.













































Let's personalize your content