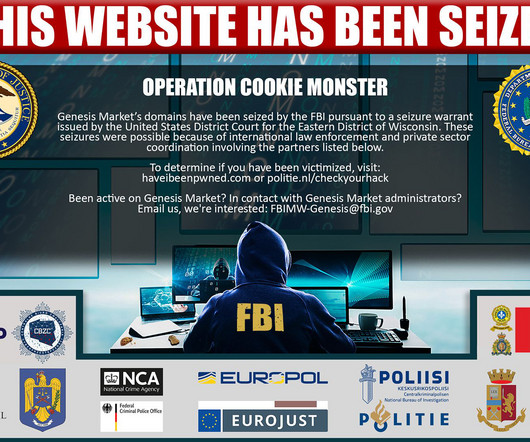
Seized Genesis Market Data is Now Searchable in Have I Been Pwned, Courtesy of the FBI and "Operation Cookie Monster"
Troy Hunt
APRIL 5, 2023
You've probably seen stories and infographics about how much your personal information is worth, both to legitimate organisations and criminal networks. In its simplest form, the illegal data marketplace has long involved the exchange of currency for personal records containing attributes such as email addresses, passwords, names, etc.





















Let's personalize your content