FBI deleted China-linked PlugX malware from over 4,200 US computers
Security Affairs
JANUARY 14, 2025
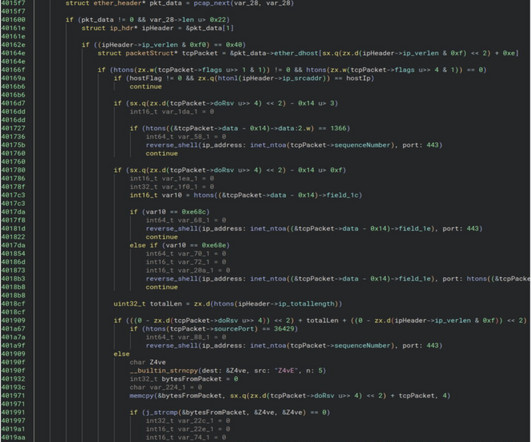
The FBI has removed Chinese PlugX malware from over 4,200 computers in networks across the United States, the U.S. The Justice Department and FBI, along with international partners, announced they deleted PlugX malware from thousands of infected computers worldwide as part of a multi-month law enforcement operation.







Let's personalize your content