COVID-19: Latest Security News & Commentary
Dark Reading
MARCH 31, 2020
Check out Dark Reading's updated, exclusive news and commentary surrounding the coronavirus pandemic.

 latest-commentary
latest-commentary 
Dark Reading
MARCH 31, 2020
Check out Dark Reading's updated, exclusive news and commentary surrounding the coronavirus pandemic.

Dark Reading
MARCH 31, 2020
Check out Dark Reading's updated, exclusive news and commentary surrounding the coronavirus pandemic.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
OCTOBER 21, 2022
Here’s the latest: a training-time attack that forces the model to exhibit a point of view: Spinning Language Models: Risks of Propaganda-As-A-Service and Countermeasures.” Machine learning security is extraordinarily difficult because the attacks are so varied—and it seems that each new one is weirder than the next.

BH Consulting
APRIL 18, 2024
The big picture commentary tends to veer between positive and negative takes on where this is all going. Every month we send out the latest cybersecurity and data protection news, trends and advice from around the globe. SANS Institute tries to balance the potential for innovation with the possibility of risk.

eSecurity Planet
APRIL 23, 2021
Depending on your interests, you can catch up on the latest news and hear analysis from experts in the field, or you can take a deep-dive into a major cybersecurity story or concept. In this podcast, Dave Bittner summarizes the latest stories you need to know with clear and concise reporting. The best part? Hacking Humans.

SecureWorld News
JULY 13, 2023
In its latest research , SlashNext—a provider of multi-channel phishing and human hacking solutions—delves into the emerging use of generative AI, including OpenAI's ChatGPT, and the cybercrime tool WormGPT, in Business Email Compromise (BEC) attacks.
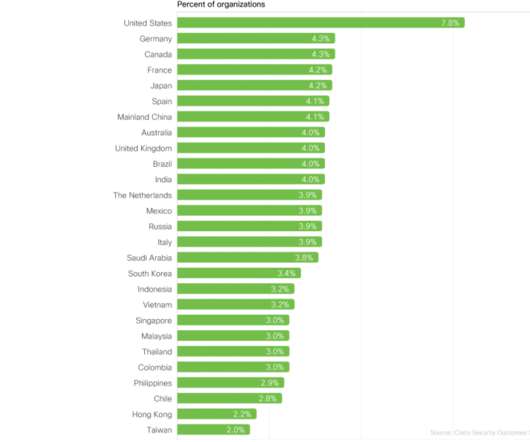
Cisco Security
DECEMBER 7, 2021
Our latest cybersecurity research study suggests that this is not only true but is also a tangible reality for organizations that choose to follow some practical steps. What if you could build a successful, world-class security program with just five practices? . And as those blogs become available, they’ll be linked below.
Let's personalize your content