KrebsOnSecurity Hit By Huge New IoT Botnet “Meris”
Krebs on Security
SEPTEMBER 10, 2021
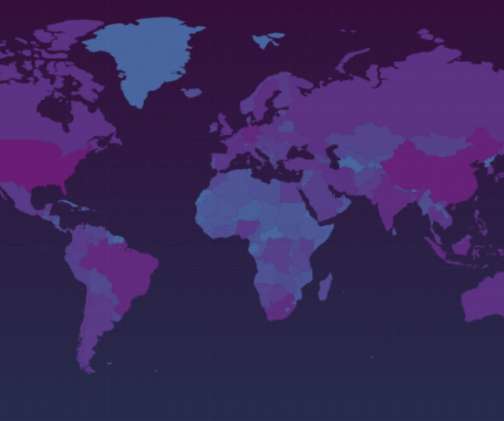
The assault came from “ Meris ,” the same new “Internet of Things” (IoT) botnet behind record-shattering attacks against Russian search giant Yandex this week and internet infrastructure firm Cloudflare earlier this summer. The darker areas indicate larger concentrations of potentially vulnerable MikroTik routers.












































Let's personalize your content