Software firm AnyDesk disclosed a security breach
Security Affairs
FEBRUARY 4, 2024
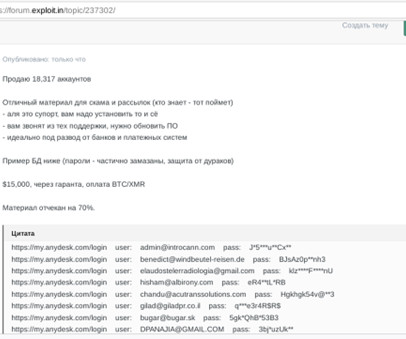
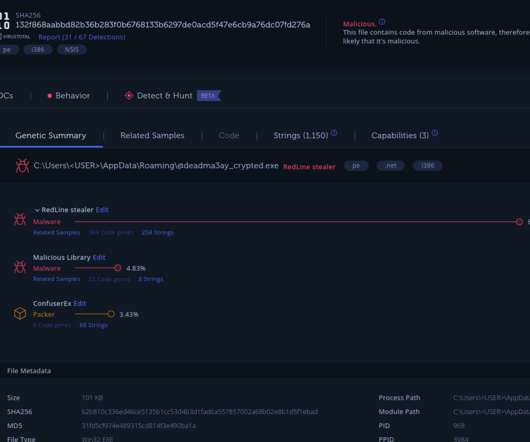
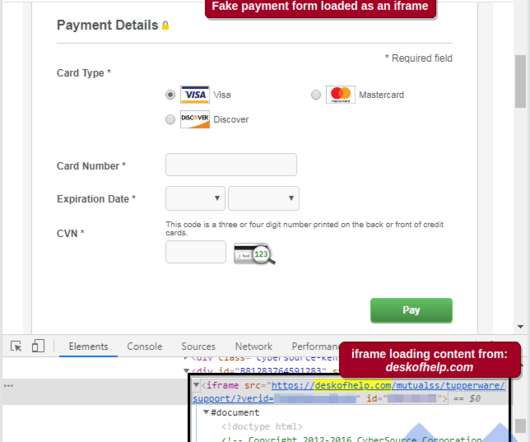
Remote desktop software company AnyDesk announced that threat actors compromised its production environment. Remote desktop software company AnyDesk announced on Friday that threat actors had access to its production systems. AnyDesk did not reveal if it has suffered a data breach.












































Let's personalize your content